Proxy Site One, a gateway to a world of online anonymity and security, offers users a unique way to navigate the internet. This technology acts as an intermediary, shielding your true identity and location while accessing websites and online services. Imagine a virtual cloak that allows you to browse the web without leaving a trace, providing a layer of privacy and protection from prying eyes.
Proxy sites have become increasingly popular for their ability to bypass censorship, access blocked content, and enhance online security. They work by routing your internet traffic through a proxy server, masking your IP address and location. Whether you’re concerned about online privacy, seeking to access geo-restricted content, or simply want to enhance your browsing experience, proxy sites offer a range of benefits.
Types of Proxy Sites
Proxy sites are servers that act as intermediaries between your computer and the internet, masking your IP address and potentially enhancing your privacy and security. They offer a variety of functionalities, catering to different needs.
Types of Proxy Sites
Proxy sites can be categorized based on their functionality, each offering distinct advantages and disadvantages.
- Anonymous Proxies: These proxies hide your IP address, making it difficult to trace your online activities back to you. They are often used for privacy and security reasons, as well as for accessing geo-restricted content.
- Advantages: Increased privacy and security, access to geo-restricted content.
- Disadvantages: Slower speeds, potential for security risks if the proxy is compromised.
- Transparent Proxies: These proxies do not hide your IP address, but they can still be used to bypass firewalls and access blocked websites. They are often used by businesses to allow employees to access specific websites that are blocked on their corporate network.
- Advantages: Faster speeds, increased security (as your IP address is not hidden).
- Disadvantages: No privacy protection, limited use cases.
- Web Proxies: These proxies are designed to be used by anyone and are typically accessed through a web browser. They offer a simple way to access blocked websites or improve privacy, but they are often less secure than other types of proxies.
- Advantages: Easy to use, often free.
- Disadvantages: Lower security, potentially slower speeds.
Proxy Site Security and Privacy
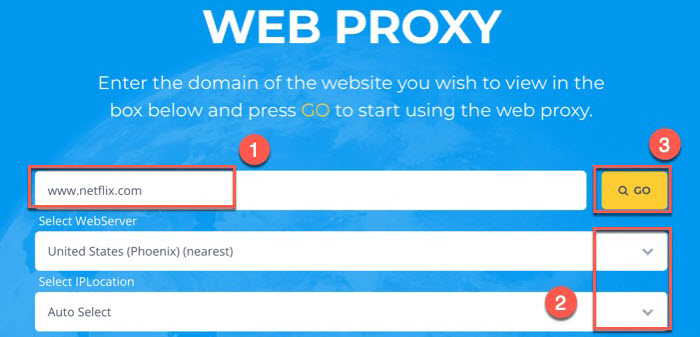
Proxy sites offer a way to browse the internet anonymously and bypass geo-restrictions. However, using a proxy site comes with security and privacy risks. Understanding these risks and how to mitigate them is crucial for safe and secure internet browsing.
Potential Security Risks
Proxy sites can be vulnerable to security risks, including:
- Man-in-the-middle attacks: A malicious actor can intercept the communication between your device and the proxy server, potentially stealing your data, such as login credentials or credit card information.
- Data breaches: If the proxy site itself is compromised, your data may be exposed to unauthorized access. This can happen if the site is not adequately secured or if it falls victim to a cyberattack.
- Malware infections: Some proxy sites may host malicious software that can infect your device. This could happen if you visit a compromised proxy site or download a file from a proxy site that contains malware.
- Tracking and monitoring: Some proxy sites may track your browsing activity and sell your data to advertisers or third parties. This can be a privacy concern, as it allows others to learn about your online behavior.
Protecting User Privacy
Proxy sites can also offer privacy benefits by:
- Hiding your IP address: A proxy site masks your real IP address, making it difficult for websites to track your location and browsing history.
- Enhancing anonymity: Using a proxy site can make it more difficult for websites to identify you, especially if you use a combination of proxy sites and other privacy tools.
- Bypassing censorship: Proxy sites can allow you to access blocked websites, such as social media platforms or news sites that are censored in certain countries.
Choosing a Safe and Reliable Proxy Site
Here are some tips for choosing a safe and reliable proxy site:
- Choose a reputable proxy site: Look for a site that has a good reputation and positive reviews from other users. Avoid using free proxy sites, as they are more likely to be compromised.
- Use a secure proxy site: Ensure the proxy site uses HTTPS encryption to protect your data from eavesdropping. Look for a padlock icon in your browser’s address bar.
- Read the proxy site’s privacy policy: Understand how the proxy site collects and uses your data. Look for a site that has a clear and transparent privacy policy.
- Use a VPN: A VPN (virtual private network) offers a more secure and private way to browse the internet than a proxy site. A VPN encrypts all of your internet traffic and routes it through a secure server, making it more difficult for websites and hackers to track your online activity.
Proxy Sites and Censorship
Proxy sites are often used to bypass internet censorship, allowing users to access websites and content that are blocked in their region. This is particularly relevant in countries with strict internet controls, where access to information is restricted.
Circumventing Censorship
Proxy sites act as intermediaries between users and the internet. When a user requests a website through a proxy, the request is routed through the proxy server instead of directly to the website. The proxy server then retrieves the requested content and forwards it to the user, effectively hiding the user’s location and identity. This makes it difficult for internet censorship mechanisms to block access to the desired content.
Ethical Implications
The use of proxy sites to access blocked content raises ethical considerations. While it can be argued that individuals have a right to access information freely, using proxy sites to circumvent censorship can also be seen as undermining the authority of governments and potentially facilitating the spread of harmful or illegal content.
Examples of Censorship Circumvention
Proxy sites are commonly used in countries with strict internet censorship, such as:
- China: The Chinese government operates the “Great Firewall,” which blocks access to numerous websites, including social media platforms, news outlets, and political websites. Proxy sites are widely used in China to circumvent these restrictions.
- Iran: The Iranian government heavily censors the internet, blocking access to websites deemed politically sensitive or morally objectionable. Proxy sites are used by Iranian citizens to access blocked content, including social media platforms and news websites.
- North Korea: North Korea has one of the most restrictive internet policies in the world, with limited access to the outside world. Proxy sites are used by a select few individuals who have access to the internet to bypass censorship and access information from outside the country.
The Future of Proxy Sites
The world of proxy sites is constantly evolving, influenced by the rapid advancements in technology. These advancements will significantly shape the future of proxy sites, impacting their development, usage, and overall role in a more connected world.
Impact of Emerging Technologies
The emergence of new technologies, such as blockchain, artificial intelligence (AI), and quantum computing, will likely have a profound impact on proxy sites.
- Blockchain Technology: Blockchain technology can be leveraged to create decentralized proxy networks, eliminating the need for a central server. This would enhance privacy and security by distributing data across multiple nodes, making it more difficult for attackers to compromise the network.
- Artificial Intelligence (AI): AI can be used to develop sophisticated proxy detection and bypass techniques, making it harder for websites to identify and block proxy users. AI can also be used to optimize proxy performance, ensuring faster connection speeds and better user experience.
- Quantum Computing: Quantum computing has the potential to revolutionize cryptography, making current encryption methods obsolete. This could impact the security of proxy sites, requiring the development of new encryption algorithms to protect user data.
Future Trends in Proxy Site Development and Usage
The future of proxy sites will see a shift towards more specialized and customized services.
- Specialized Proxy Services: Proxy sites will cater to specific needs, such as streaming, gaming, or accessing geo-restricted content. For example, streaming proxy services could offer optimized connections for specific platforms like Netflix or Hulu.
- Personalized Proxy Experiences: Proxy sites will personalize user experiences based on their individual preferences and usage patterns. This could include features like automatic proxy selection based on location, content type, or desired level of privacy.
- Increased Focus on Security and Privacy: Proxy sites will prioritize user security and privacy by implementing robust encryption protocols, anonymous browsing features, and strict data retention policies. This will become increasingly important as users become more aware of data privacy concerns.
Role of Proxy Sites in a More Connected World
As the internet becomes more interconnected and globalized, proxy sites will play a crucial role in bridging the digital divide and fostering a more inclusive online environment.
- Overcoming Censorship: Proxy sites will continue to be vital tools for circumventing censorship and accessing blocked content in countries with restrictive internet policies. This will allow individuals to access information and express themselves freely, promoting freedom of speech and expression.
- Protecting User Privacy: Proxy sites will provide users with an extra layer of protection against online tracking and surveillance. This is particularly important in an era of increasing data collection and government surveillance.
- Facilitating Global Collaboration: Proxy sites will enable users to access online resources and collaborate with individuals from different parts of the world, regardless of their location or internet restrictions. This will foster innovation and knowledge sharing across borders.
Alternatives to Proxy Sites: Proxy Site One
Proxy sites offer a way to browse the internet anonymously and bypass geo-restrictions, but they aren’t the only solution. Several alternatives provide similar functionalities with their own unique advantages and disadvantages.
Virtual Private Networks (VPNs), Proxy site one
VPNs are a popular alternative to proxy sites. They encrypt your internet traffic and route it through a server in a different location, masking your IP address and location.
- Enhanced Security: VPNs provide a higher level of security than proxy sites by encrypting all your internet traffic, not just specific websites. This protects your data from eavesdroppers and malicious actors.
- Improved Privacy: VPNs mask your IP address and location, making it harder for websites and advertisers to track your online activity.
- Bypass Geo-restrictions: VPNs allow you to access websites and content that are blocked in your region by connecting to a server in a different country.
- Increased Speed: Some VPNs offer faster speeds than proxy sites, especially when using servers close to your location.
However, VPNs can be more expensive than proxy sites and require a subscription. Some VPNs also have limited bandwidth or data caps.
The Onion Router (Tor)
Tor is a free and open-source software that routes your internet traffic through a network of relays, making it difficult to track your online activity.
- Strong Anonymity: Tor provides a high level of anonymity by bouncing your traffic through multiple relays, making it challenging to identify your location or IP address.
- Bypass Censorship: Tor is often used to access blocked websites and content in countries with strict internet censorship.
- Privacy Protection: Tor helps protect your privacy by making it difficult for websites and advertisers to track your online activity.
Tor can be slower than proxy sites and VPNs, and it’s not always reliable. Tor is also known for its association with illegal activities, which can make it difficult to use for legitimate purposes.
Dedicated Servers
Dedicated servers provide a high level of control and customization for your online activities. You can configure a dedicated server to act as a proxy or VPN, allowing you to access blocked websites and content and protect your privacy.
- Complete Control: Dedicated servers give you complete control over your online environment, allowing you to customize security settings and configure access permissions.
- High Performance: Dedicated servers offer high performance and speed, ideal for demanding tasks such as streaming or gaming.
- Scalability: You can easily scale your dedicated server to meet your growing needs.
Dedicated servers are expensive and require technical expertise to manage. They also come with a higher level of responsibility, as you are responsible for maintaining the security and integrity of your server.
Comparison Table
| Feature | Proxy Sites | VPNs | Tor | Dedicated Servers |
|---|---|---|---|---|
| Security | Basic | High | High | High |
| Privacy | Moderate | High | High | High |
| Speed | Variable | Variable | Slow | High |
| Cost | Free or low-cost | Subscription-based | Free | Expensive |
| Ease of Use | Easy | Easy | Moderate | Difficult |
Case Studies of Proxy Site Usage
Proxy sites offer a wide range of applications, impacting individuals, businesses, and organizations in various ways. Understanding real-world examples helps illustrate the diverse uses and implications of proxy site usage.
Proxy Sites for Accessing Blocked Content
Proxy sites are often used to bypass geo-restrictions and access content blocked in specific geographical locations.
- Streaming Services: Individuals in countries where Netflix or other streaming services are not available can use proxy sites to access content libraries restricted to specific regions. For example, a user in India might use a proxy site to access Netflix’s US library, gaining access to a wider range of movies and TV shows.
- Social Media Platforms: In countries with strict internet censorship, individuals might use proxy sites to access social media platforms like Facebook, Twitter, or YouTube, which may be blocked by government authorities.
Proxy Sites for Privacy and Security
Proxy sites can enhance online privacy and security by masking the user’s IP address and location.
- Protecting Online Identity: Individuals concerned about their online privacy might use proxy sites to hide their IP address and location, making it more difficult for websites and advertisers to track their browsing activity.
- Accessing Public Wi-Fi Safely: When using public Wi-Fi networks, which can be vulnerable to security threats, proxy sites can encrypt user traffic, making it harder for hackers to intercept sensitive data.
Proxy Sites for Business and Organizational Applications
Proxy sites are employed by businesses and organizations for various purposes, including web filtering, content access control, and security enhancement.
- Web Filtering and Content Control: Companies can use proxy sites to block access to websites that are not relevant to work or that may pose security risks, enhancing productivity and protecting company data.
- Accessing Restricted Resources: Businesses with offices in different geographical locations can use proxy sites to provide employees with access to company resources, such as internal networks or databases, that might be restricted based on location.
- Improving Network Security: Proxy sites can act as an intermediary between users and the internet, filtering traffic and protecting internal networks from malicious attacks.
Proxy Sites for Research and Academic Purposes
Proxy sites are often used in academic research and scholarly activities, particularly in areas where access to specific resources or data is restricted.
- Accessing Research Databases: Researchers might use proxy sites to access subscription-based research databases that are not available to the general public.
- Bypassing Content Restrictions: Researchers working on sensitive topics or in countries with censorship might use proxy sites to access information that is restricted or blocked.
Closing Summary
In conclusion, proxy sites have revolutionized the way we interact with the internet, offering a myriad of advantages for both individuals and businesses. From enhancing online privacy to bypassing censorship and improving network security, proxy sites have become an essential tool in today’s digital landscape. However, it’s crucial to choose a reputable and reliable proxy site to ensure your online safety and privacy. As technology continues to evolve, proxy sites are expected to play an even more prominent role in shaping the future of the internet, empowering users with greater control and security in the digital realm.



