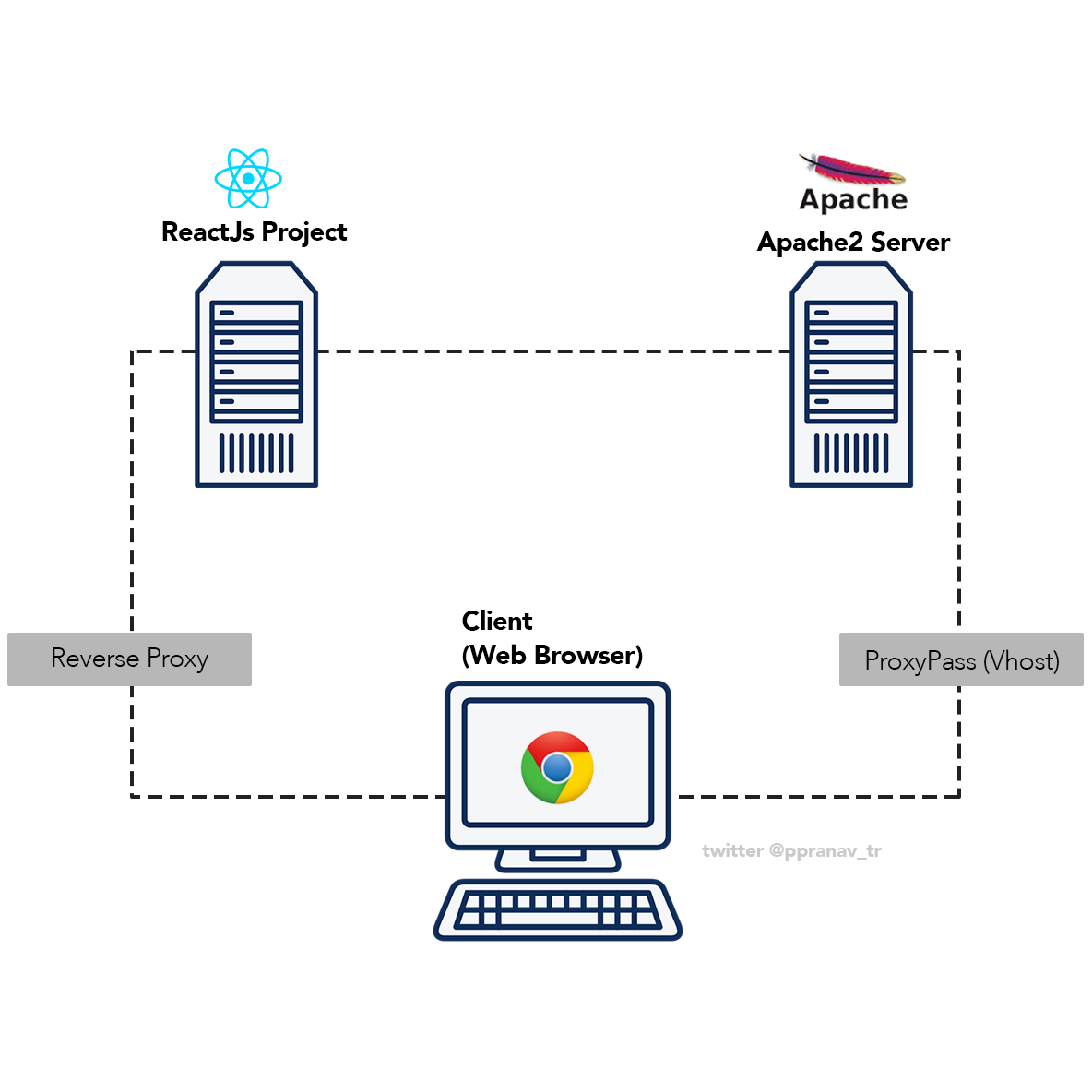
Client server computing – Client-server computing, at its core, is a revolutionary architecture that fundamentally changed how we interact with technology. This model, where dedicated servers handle requests from multiple clients, has become the foundation for a vast array of applications and services we use daily. From web browsing to online gaming, client-server computing seamlessly connects users to vast amounts of data and resources, transforming how we work, learn, and entertain ourselves.
Imagine a world where every user had to manage their own data and applications – it would be chaotic and inefficient. Client-server computing solves this by centralizing data and resources, enabling seamless sharing and access for everyone. The server acts as a powerful central hub, while clients, like our computers and smartphones, act as access points, enabling us to utilize these resources.
Introduction to Client-Server Computing
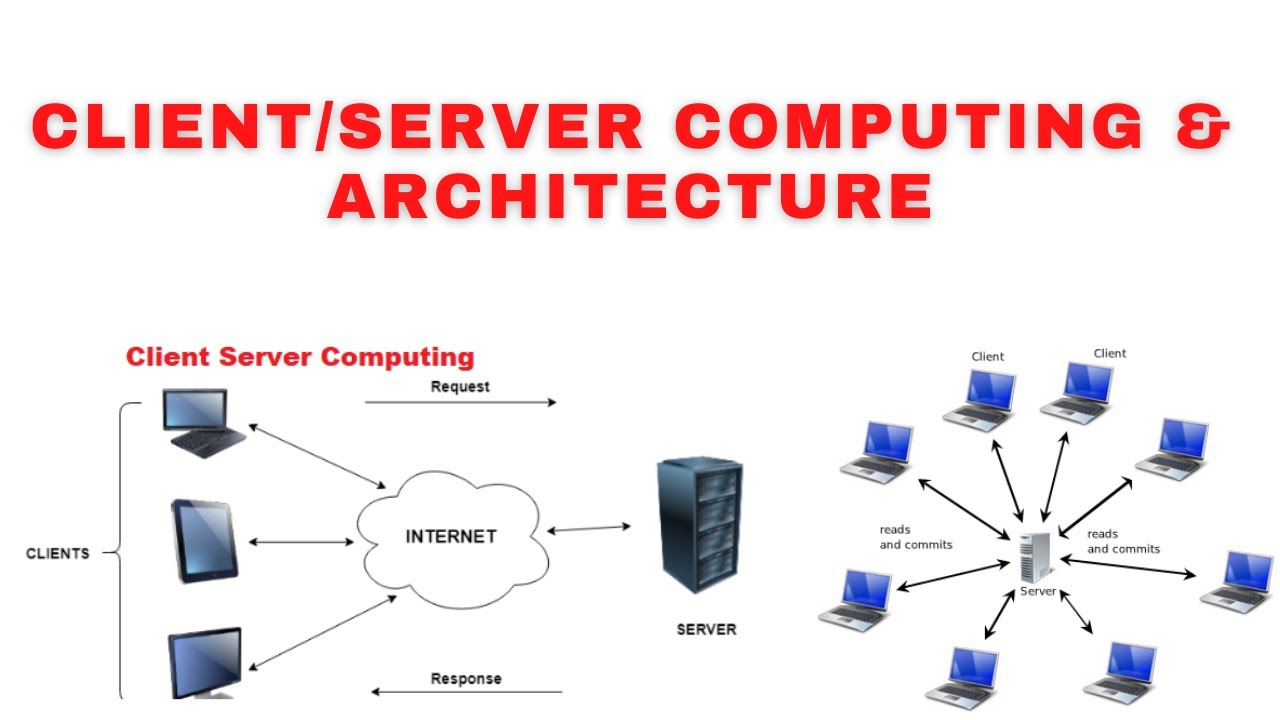
Client-server computing is a ubiquitous model for distributing applications and resources across a network. This architecture separates functionalities between clients and servers, enabling efficient collaboration and resource sharing.
Client-Server Architecture
Client-server architecture describes a network structure where a client application requests services from a server application. The server, typically a powerful computer with dedicated resources, provides these services to multiple clients simultaneously.
Roles and Responsibilities
Clients and servers have distinct roles and responsibilities in a client-server system:
Clients
- Request services: Clients initiate requests to the server for specific services, such as accessing data, performing calculations, or retrieving information.
- Receive responses: After sending a request, clients wait for the server to process it and send back a response.
- Interact with users: Clients provide a user interface for users to interact with the server’s services.
Servers
- Provide services: Servers offer various services to clients, such as data storage, file sharing, web hosting, email services, and more.
- Process requests: Servers receive requests from clients, process them, and generate responses.
- Manage resources: Servers manage resources like storage, processing power, and network connections to ensure efficient service delivery.
Examples of Client-Server Applications
Client-server applications are widespread in various domains. Some common examples include:
Web Browsing
- Client: Web browser (e.g., Chrome, Firefox, Safari)
- Server: Web server (e.g., Apache, Nginx)
When you visit a website, your web browser (client) sends a request to the web server hosting the website. The server processes the request and sends back the website’s content, which your browser displays.
- Client: Email client (e.g., Outlook, Gmail, Thunderbird)
- Server: Email server (e.g., Exchange, Postfix)
When you send an email, your email client (client) connects to the email server and sends the email message. The server then routes the email to the recipient’s email server.
Online Banking
- Client: Online banking application (e.g., mobile app, web portal)
- Server: Bank’s server
When you access your online banking account, the banking application (client) connects to the bank’s server to retrieve account information, perform transactions, and manage your finances.
File Sharing
- Client: File sharing application (e.g., Dropbox, Google Drive)
- Server: File sharing server
File sharing applications allow you to store and share files online. The client application connects to the file sharing server to upload, download, and manage your files.
Advantages of Client-Server Computing
Client-server computing offers a range of advantages over traditional peer-to-peer systems, making it a preferred choice for many applications. The benefits stem from its centralized architecture, which enables efficient data management, resource sharing, and enhanced security.
Centralized Data Management and Resource Sharing
Centralized data management in a client-server system offers numerous advantages, simplifying data access, administration, and resource utilization.
- Simplified Data Access: All data is stored centrally on the server, making it easily accessible to authorized clients. This eliminates the need for clients to store data locally, simplifying data management and reducing redundancy.
- Enhanced Data Consistency: Centralized data storage ensures data consistency across all clients. Changes made to the data on the server are immediately reflected on all connected clients, eliminating the possibility of data conflicts or inconsistencies.
- Improved Data Security: Centralized data storage allows for better security measures, as access control and data encryption can be implemented at the server level. This reduces the risk of data breaches and unauthorized access.
- Streamlined Administration: Server administrators can manage and update data from a single location, simplifying maintenance tasks and reducing administrative overhead.
- Efficient Resource Sharing: Client-server systems allow for the sharing of resources such as software, hardware, and data among multiple clients. This eliminates the need for individual clients to purchase and maintain their own resources, leading to cost savings and increased efficiency.
Enhanced Security and Scalability
Client-server architecture offers enhanced security and scalability compared to traditional peer-to-peer systems.
- Improved Security: The centralized nature of client-server systems allows for the implementation of robust security measures at the server level. Access control, authentication, and encryption can be applied to the server, ensuring that only authorized users can access the data and resources. This provides a higher level of security compared to peer-to-peer systems, where data is stored and accessed locally on individual computers.
- Scalability: Client-server systems can be easily scaled to accommodate growing user bases and data volumes. As the number of clients increases, the server resources can be upgraded to handle the increased load. This scalability makes client-server systems suitable for large organizations with numerous users and data-intensive applications.
Collaboration and Resource Utilization
Client-server computing promotes collaboration and efficient resource utilization by providing a platform for shared access to data and resources.
- Enhanced Collaboration: Client-server systems facilitate collaboration by providing a shared platform for data and resource access. Users can work on the same data, share documents, and communicate with each other, leading to improved teamwork and productivity.
- Optimized Resource Utilization: By centralizing resources on the server, client-server systems enable efficient resource utilization. Clients can access and share resources without the need for individual installations, leading to cost savings and reduced hardware requirements.
Disadvantages of Client-Server Computing: Client Server Computing
While client-server computing offers numerous advantages, it also comes with certain disadvantages that need to be considered. These drawbacks can impact the performance, security, and overall efficiency of the system.
Network Dependence
Client-server systems rely heavily on a stable and reliable network connection. Network outages or disruptions can severely affect the availability and functionality of the system. For example, if the network connection between a client and server is lost, users will be unable to access the server’s resources, and any ongoing tasks might be interrupted. This can lead to significant downtime and productivity loss.
Single Point of Failure
The server in a client-server architecture is a single point of failure. If the server malfunctions or becomes unavailable, all clients connected to it will lose access to the shared resources. This can lead to significant disruption and data loss. For instance, if a company’s primary database server fails, all employees relying on that server will be unable to access their data, potentially causing a halt in operations.
Complexity of Management and Maintenance
Client-server systems can be complex to manage and maintain. The administration tasks involved in managing the server, network infrastructure, and client applications require specialized skills and resources. Regular updates, security patches, and system monitoring are essential to ensure the stability and security of the system. This complexity can increase the costs associated with system administration and maintenance.
Performance Bottlenecks and Resource Contention
As the number of clients accessing the server increases, performance bottlenecks and resource contention can occur. If the server’s resources are insufficient to handle the load, response times can slow down, leading to user frustration and reduced productivity. For example, if a large number of users try to access a shared file on the server simultaneously, the server might struggle to process all the requests, resulting in delays and potential data corruption.
Security Considerations in Client-Server Computing
Client-server systems, while offering numerous advantages, are also susceptible to various security threats. These systems are complex, involving multiple components and communication channels, which can create vulnerabilities for malicious actors.
Common Security Threats
The interconnected nature of client-server systems presents several security threats. These threats can be broadly categorized as:
- Data Breaches: Unauthorized access to sensitive data stored on servers is a major concern. This can involve data theft, modification, or deletion, leading to financial losses, reputational damage, and legal issues.
- Denial of Service (DoS) Attacks: These attacks aim to disrupt the availability of services by overwhelming servers with excessive traffic, making them unresponsive to legitimate users.
- Malware Infections: Malicious software can infect clients or servers, compromising system integrity and potentially stealing data or launching further attacks.
- Unauthorized Access: Hackers can attempt to gain unauthorized access to client-server systems through weak passwords, unpatched vulnerabilities, or social engineering techniques.
- Man-in-the-Middle Attacks: Attackers intercept communication between clients and servers, potentially stealing data or injecting malicious code.
Security Measures
To mitigate these threats, client-server systems employ various security measures:
- Firewalls: Firewalls act as barriers between networks, filtering incoming and outgoing traffic based on predefined rules. They prevent unauthorized access and block malicious traffic.
- Encryption: Encryption transforms data into an unreadable format, protecting it during transmission and storage. This ensures that even if data is intercepted, it cannot be understood without the decryption key.
- Authentication Protocols: These protocols verify the identity of users and devices before granting access to resources. Common protocols include Kerberos, OAuth, and OpenID Connect.
Best Practices for Securing Client-Server Applications, Client server computing
Implementing best practices is crucial for ensuring the security of client-server applications. Some key recommendations include:
- Strong Password Policies: Enforce strong password requirements, including length, complexity, and regular changes.
- Regular Security Audits: Conduct periodic security audits to identify and address vulnerabilities.
- Patch Management: Keep systems and applications updated with the latest security patches to fix known vulnerabilities.
- Data Backup and Recovery: Implement robust data backup and recovery procedures to mitigate the impact of data loss or corruption.
- Secure Coding Practices: Employ secure coding practices to minimize vulnerabilities in application code.
- User Awareness Training: Educate users about security threats and best practices for safe online behavior.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code.
- Security Monitoring and Logging: Monitor system activity and log events to detect suspicious behavior and investigate security incidents.
Client-Server Architecture in Web Development
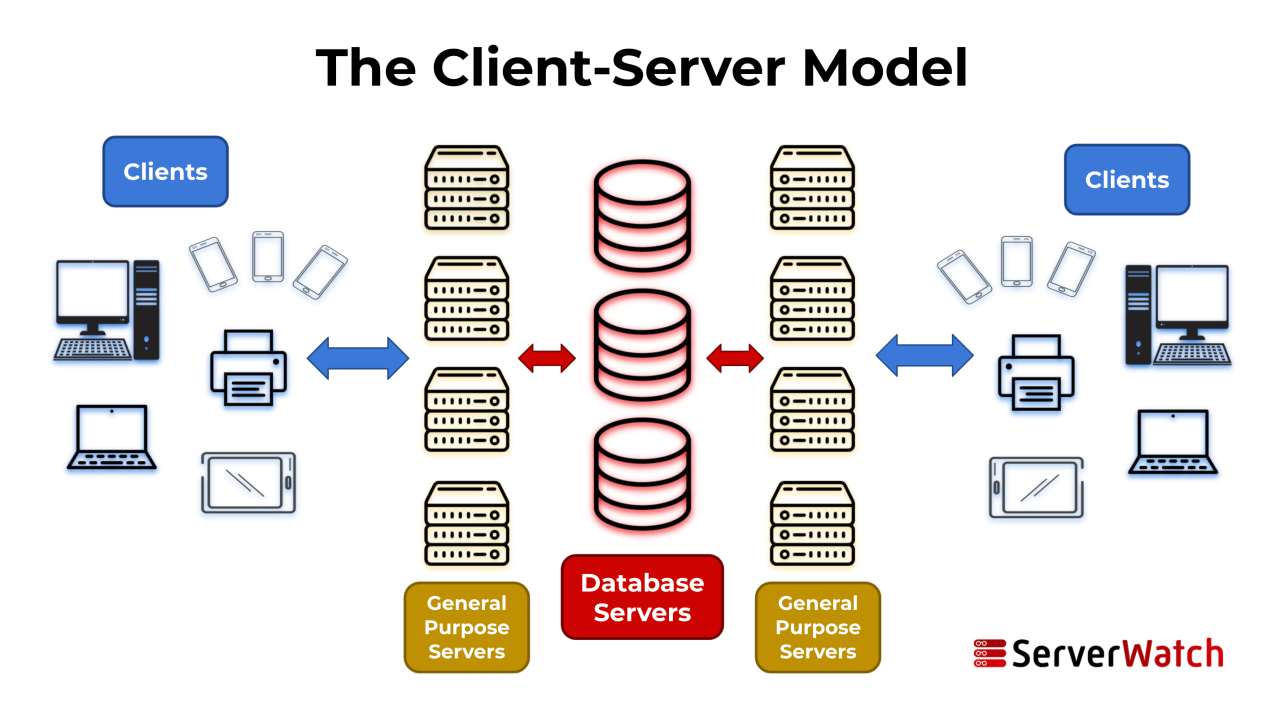
The client-server model is the foundation of how most websites and web applications function. It involves a user’s computer (the client) requesting information from a remote server that stores the website’s data and code. This architecture enables users to access web content from anywhere with an internet connection.
Role of Web Servers and Databases
Web servers and databases play crucial roles in web application functionality. Web servers act as intermediaries, receiving requests from clients and sending back responses, typically HTML pages, images, and other web resources. Databases store the website’s data, such as user information, product catalogs, and content management systems.
The web server processes the client request, retrieves the necessary data from the database, generates the HTML page, and sends it back to the client’s browser.
Handling User Requests and Delivering Web Content
The process of handling user requests and delivering web content in a client-server architecture involves the following steps:
1. Request: When a user types a website address into their browser or clicks on a link, their browser sends a request to the web server hosting the website.
2. Processing: The web server receives the request and interprets it, determining which resource the client is requesting.
3. Database Interaction: If the request requires data from the database, the web server queries the database, retrieves the necessary information, and formats it for presentation.
4. Response Generation: The web server assembles the requested web page, including HTML code, images, and other resources, and generates a response to the client.
5. Delivery: The web server sends the response back to the client’s browser, which displays the web page to the user.
Popular Web Server Technologies
Several popular web server technologies are widely used in web development, each with its strengths and weaknesses:
- Apache: Apache is an open-source web server known for its stability, flexibility, and extensive module support. It’s highly configurable and widely used, especially for hosting static websites and applications.
- Nginx: Nginx is another open-source web server gaining popularity for its high performance and efficiency in handling a large number of concurrent connections. It’s often used for serving static content, load balancing, and reverse proxying.
- Microsoft IIS: Microsoft Internet Information Services (IIS) is a web server included with Microsoft Windows operating systems. It’s commonly used for hosting websites and web applications built on Microsoft technologies, such as ASP.NET.
Concluding Remarks
The evolution of client-server computing continues to shape the technological landscape, with advancements in cloud computing and mobile technologies further pushing its boundaries. As we navigate a world increasingly reliant on interconnected systems, understanding the principles of client-server architecture becomes essential. Whether you’re a developer, a tech enthusiast, or simply a curious user, grasping the intricacies of this fundamental model unlocks a deeper understanding of the digital world we inhabit.