TFTPd32 is a powerful and versatile TFTP server that enables efficient file transfer over a network. It provides a user-friendly interface for uploading and downloading files, making it an ideal choice for various tasks, including firmware updates, network configuration, and data backups.
The Trivial File Transfer Protocol (TFTP) is a simple protocol designed for transferring files between computers on a network. It was developed as a lightweight alternative to more complex protocols like FTP. While TFTP lacks the robust features of FTP, its simplicity and ease of implementation have made it a popular choice for specific use cases. TFTPd32 leverages the TFTP protocol to provide a reliable and efficient file transfer solution.
Introduction to TFTPd32
TFTPd32 is a free and open-source application designed for transferring files over the Trivial File Transfer Protocol (TFTP). It serves as a TFTP server, enabling the transfer of files between computers on a network. TFTPd32 is known for its simplicity and ease of use, making it a popular choice for tasks that require basic file transfer capabilities.
The TFTP Protocol
The Trivial File Transfer Protocol (TFTP) is a simple network protocol designed for transferring files between computers. It was initially developed as a lightweight alternative to the more complex File Transfer Protocol (FTP). TFTP operates at the application layer of the TCP/IP model and utilizes the User Datagram Protocol (UDP) for communication.
- TFTP was introduced in 1980 as part of the early development of the Internet. It was designed to be simple and efficient, making it suitable for tasks such as booting computers from network servers.
- The protocol uses a minimal set of commands and data packets, making it lightweight and suitable for environments with limited resources.
- TFTP operates in a stateless manner, meaning that each transfer is independent and does not require a persistent connection between the client and server.
- TFTP is widely used in embedded systems, network devices, and network boot processes, where simplicity and efficiency are crucial.
Key Features and Benefits of TFTPd32
TFTPd32 provides a range of features and benefits that make it a versatile and valuable tool for network administrators and developers.
- Ease of Use: TFTPd32 is renowned for its user-friendly interface, making it easy to set up and configure. Its intuitive design allows users to quickly start and stop the server and manage file transfers.
- Lightweight and Efficient: TFTPd32 is a lightweight application with minimal resource requirements, making it suitable for systems with limited resources. Its efficiency ensures fast and reliable file transfers.
- Cross-Platform Compatibility: TFTPd32 is available for various operating systems, including Windows, Linux, and macOS. This cross-platform compatibility ensures that it can be used in diverse network environments.
- Security Features: TFTPd32 includes security features such as password protection and access control lists (ACLs) to restrict access to the server and its files. These features help to protect sensitive data and prevent unauthorized access.
- Customizable Settings: TFTPd32 offers customizable settings that allow users to tailor the server’s behavior to their specific needs. These settings include options for configuring the server’s port, timeout values, and file transfer limits.
- Open Source and Free: TFTPd32 is an open-source application, meaning that its source code is freely available for examination, modification, and distribution. This open-source nature fosters community involvement and encourages improvements to the software.
Security Considerations
TFTP, despite its simplicity, is inherently insecure. This is because it lacks any built-in authentication or encryption mechanisms. Consequently, using TFTPd32 without appropriate security measures can expose your system to various vulnerabilities. Understanding these vulnerabilities and implementing mitigation strategies is crucial for safeguarding your network and data.
Potential Vulnerabilities, Tftpd32
The absence of security features in TFTP makes it susceptible to various attacks. Here are some common vulnerabilities and their implications:
- Man-in-the-Middle (MitM) Attacks: Since TFTP transmissions are unencrypted, attackers can intercept and modify data packets between the client and server. This allows them to steal sensitive information, inject malicious code, or alter the contents of transferred files.
- Denial-of-Service (DoS) Attacks: TFTP servers can be overwhelmed by a flood of requests, preventing legitimate clients from accessing the server. This can disrupt network operations and compromise critical services.
- Unauthorized Access: Without authentication, anyone can access the TFTP server and potentially download or upload files. This can lead to data breaches, system compromise, and unauthorized modifications.
Mitigation Strategies
While TFTP itself lacks inherent security, various strategies can be employed to mitigate the risks associated with using TFTPd32:
- Restrict Access: Configure TFTPd32 to only allow connections from specific IP addresses or subnets. This limits access to authorized clients and reduces the attack surface.
- Use Firewalls: Deploy firewalls to block unauthorized access to the TFTP server. Configure rules to allow only legitimate TFTP traffic, preventing malicious connections.
- Implement Network Segmentation: Isolate the TFTP server on a separate network segment, minimizing the impact of potential breaches and restricting access to critical resources.
- Use VPNs: Encrypt TFTP traffic by establishing a VPN tunnel between the client and server. This protects data in transit and prevents MitM attacks.
- Enable Secure Protocols: Consider using alternative protocols like SFTP (SSH File Transfer Protocol) or HTTPS (Hypertext Transfer Protocol Secure) that provide encryption and authentication, offering a more secure solution.
Best Practices for Securing TFTPd32 Installations
Implementing these best practices can significantly enhance the security of your TFTPd32 installation:
- Use Strong Passwords: If TFTPd32 supports authentication, ensure strong passwords are used to prevent unauthorized access. Avoid using common or easily guessable passwords.
- Regularly Update TFTPd32: Keep your TFTPd32 installation updated with the latest security patches to address vulnerabilities and mitigate potential exploits.
- Limit File Access: Configure TFTPd32 to restrict file access to specific directories or files. This prevents unauthorized access to sensitive data.
- Monitor TFTPd32 Activity: Regularly monitor TFTPd32 activity to identify suspicious connections or unusual patterns. This can help detect and respond to potential security threats.
- Enable Logging: Configure TFTPd32 to log all activity, including successful and failed connections, file transfers, and errors. This provides valuable information for auditing and troubleshooting security incidents.
Integration with Other Tools
TFTPd32, while a powerful tool for file transfers, can be further enhanced by integrating it with other network management tools. This integration streamlines network operations, automates tasks, and facilitates efficient troubleshooting.
Integration with Network Management Systems
Integrating TFTPd32 with network management systems (NMS) enables centralized control and monitoring of the TFTP server. This integration simplifies the administration of the TFTP server by allowing administrators to manage the server, monitor its status, and configure its settings directly from the NMS console. Popular NMS solutions like SolarWinds Network Performance Monitor, ManageEngine OpManager, and PRTG Network Monitor can be used for this purpose.
Scripting and Automation
TFTPd32 can be effectively integrated with scripting languages like Python, PowerShell, and Bash to automate routine tasks and improve efficiency. Scripts can be used to perform actions such as:
- Starting and stopping the TFTP server
- Configuring the server’s settings
- Monitoring the server’s status
- Transferring files to and from the server
For example, a Python script can be used to upload firmware files to network devices using TFTPd32, ensuring consistent and automated firmware updates across the network.
Integration with Other Protocols
TFTPd32 can be used in conjunction with other protocols to facilitate network management tasks.
- DHCP: TFTPd32 can be used to serve configuration files to network devices via DHCP. When a device boots, it sends a DHCP request to the DHCP server. The DHCP server can then use TFTPd32 to provide the device with its configuration file, including IP address, subnet mask, gateway, and DNS server settings.
- SNMP: TFTPd32 can be used to transfer configuration files to network devices that support SNMP. SNMP (Simple Network Management Protocol) is a widely used protocol for managing and monitoring network devices. TFTPd32 can be used to upload configuration files to devices, which can then be managed using SNMP tools.
- Syslog: TFTPd32 can be used to transfer log files from network devices to a central server for analysis and troubleshooting. This integration helps in centralizing log management and facilitates easier analysis of network events.
Real-World Applications
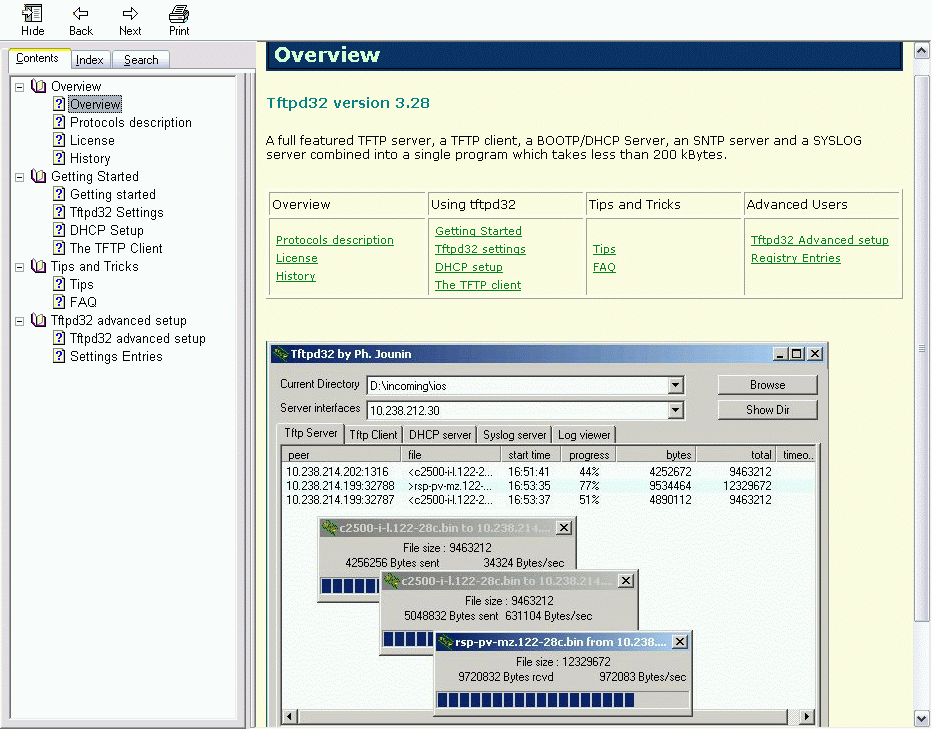
TFTPd32 finds its place in a variety of industries, serving as a vital tool for network administration, firmware updates, and data transfer. Its simplicity and reliability make it a valuable asset in various real-world scenarios.
TFTPd32 Applications in Different Industries
The following table highlights some of the key applications of TFTPd32 across various industries:
| Industry | Application | Specific Use Cases |
|---|---|---|
| Networking | Network Device Configuration | – Updating firmware on routers and switches – Configuring network devices remotely – Transferring configuration files |
| Embedded Systems | Firmware Updates | – Updating firmware on embedded devices like IoT sensors and controllers – Distributing new software releases to devices – Performing remote updates on embedded systems |
| Telecommunications | Network Management | – Managing network devices in telecommunication infrastructure – Deploying new services and features to network elements – Transferring configuration data between network devices |
| Manufacturing | Industrial Automation | – Updating firmware on industrial robots and controllers – Transferring configuration data to programmable logic controllers (PLCs) – Providing a reliable data transfer mechanism for industrial control systems |
| Education | Network Labs | – Creating network simulation environments for students – Simulating network device configurations and troubleshooting scenarios – Providing a platform for hands-on network learning experiences |
Alternatives to TFTPd32
While TFTPd32 is a popular and reliable TFTP server, several alternatives offer unique features, performance optimizations, and enhanced security. Choosing the right alternative depends on specific requirements and the project’s context.
Comparison of TFTP Server Implementations
This section compares popular TFTP server implementations, highlighting their advantages, disadvantages, and suitability for specific use cases.
- Tftpd-hpa: This implementation is a highly portable and feature-rich TFTP server, known for its stability and support for various platforms.
- Advantages:
- Highly portable, running on various operating systems.
- Offers extensive features, including support for multiple TFTP modes and options.
- Well-documented and actively maintained, ensuring continued support and updates.
- Disadvantages:
- May have a steeper learning curve compared to TFTPd32, due to its more complex configuration options.
- Might require additional setup and configuration for specific use cases.
- Suitability: Suitable for projects requiring a robust and feature-rich TFTP server, especially when portability across platforms is a priority.
- Advantages:
- Atftpd: Atftpd is a lightweight and simple TFTP server, often used for basic file transfer tasks.
- Advantages:
- Easy to install and configure, making it suitable for quick deployments.
- Minimal resource consumption, making it suitable for systems with limited resources.
- Disadvantages:
- Limited features compared to other implementations, lacking advanced options like security enhancements.
- May not be as stable or reliable as more feature-rich alternatives.
- Suitability: Ideal for simple TFTP file transfer scenarios where performance and security are not critical factors.
- Advantages:
- tftpd-server: This implementation is a part of the tftp-hpa package, offering a lightweight and efficient TFTP server optimized for speed and resource efficiency.
- Advantages:
- Highly optimized for performance, handling large file transfers efficiently.
- Low resource consumption, minimizing system overhead.
- Disadvantages:
- Limited features compared to other implementations, focusing primarily on speed and efficiency.
- May require more specialized knowledge for configuration and optimization.
- Suitability: Best suited for projects prioritizing high-speed file transfers, especially in environments with limited resources.
- Advantages:
- Tiny TFTP Server: Tiny TFTP Server is a compact and lightweight TFTP server, known for its ease of use and minimal footprint.
- Advantages:
- Extremely small size, making it suitable for embedded systems or environments with limited storage space.
- Simple to install and configure, requiring minimal effort for setup.
- Disadvantages:
- Limited features, lacking advanced options like security enhancements or support for multiple TFTP modes.
- May not be as robust or reliable as more feature-rich alternatives.
- Suitability: Ideal for simple TFTP file transfer scenarios in resource-constrained environments, where size and ease of use are critical.
- Advantages:
Future of TFTP and TFTPd32
While TFTP remains a valuable tool for specific scenarios, its role in the evolving network landscape is subject to change. As network protocols evolve and security concerns intensify, the future of TFTP and TFTPd32 hinges on adapting to these changing demands.
TFTP’s Continued Relevance
TFTP’s simplicity and ease of use continue to make it a practical choice for certain tasks, particularly in situations where:
- Limited Resources: TFTP’s lightweight nature makes it suitable for devices with constrained resources, such as embedded systems or network bootloaders.
- Basic File Transfers: For transferring small configuration files or firmware updates, TFTP’s straightforward file transfer mechanism remains efficient.
- Legacy Environments: TFTP’s long-standing presence in networking makes it a familiar option for legacy systems and protocols.
TFTPd32’s Adaptation
TFTPd32’s future depends on its ability to address emerging challenges and adapt to the evolving network landscape. Key considerations include:
- Enhanced Security: TFTPd32 needs to incorporate robust security measures, such as authentication and encryption, to mitigate vulnerabilities in its unencrypted communication.
- Integration with Modern Networks: TFTPd32 should seamlessly integrate with modern network management tools and protocols to facilitate streamlined operations.
- Improved Performance: Optimization for speed and efficiency is crucial for TFTPd32 to remain competitive in a performance-driven environment.
Final Thoughts
TFTPd32 offers a comprehensive and reliable solution for file transfer needs. Its ease of use, security features, and integration capabilities make it a valuable tool for network administrators, system engineers, and anyone involved in managing network devices. Whether you’re updating firmware, configuring network settings, or simply transferring files, TFTPd32 provides a robust and efficient way to accomplish these tasks. As the network landscape continues to evolve, TFTPd32 remains a relevant and valuable tool for managing network resources.




