HTTP Server, the unsung hero of the internet, silently orchestrates the flow of information between your browser and the vast world of websites. It acts as a bridge, receiving your requests and delivering the content you crave, making the web experience seamless and enjoyable.
Imagine the internet as a bustling city. HTTP servers are the delivery trucks, efficiently transporting packages of data (web pages, images, videos) to your doorstep (browser). They handle the intricate dance of HTTP requests and responses, ensuring a smooth exchange of information. This vital role makes HTTP servers the foundation upon which the entire web infrastructure rests.
What is an HTTP Server?
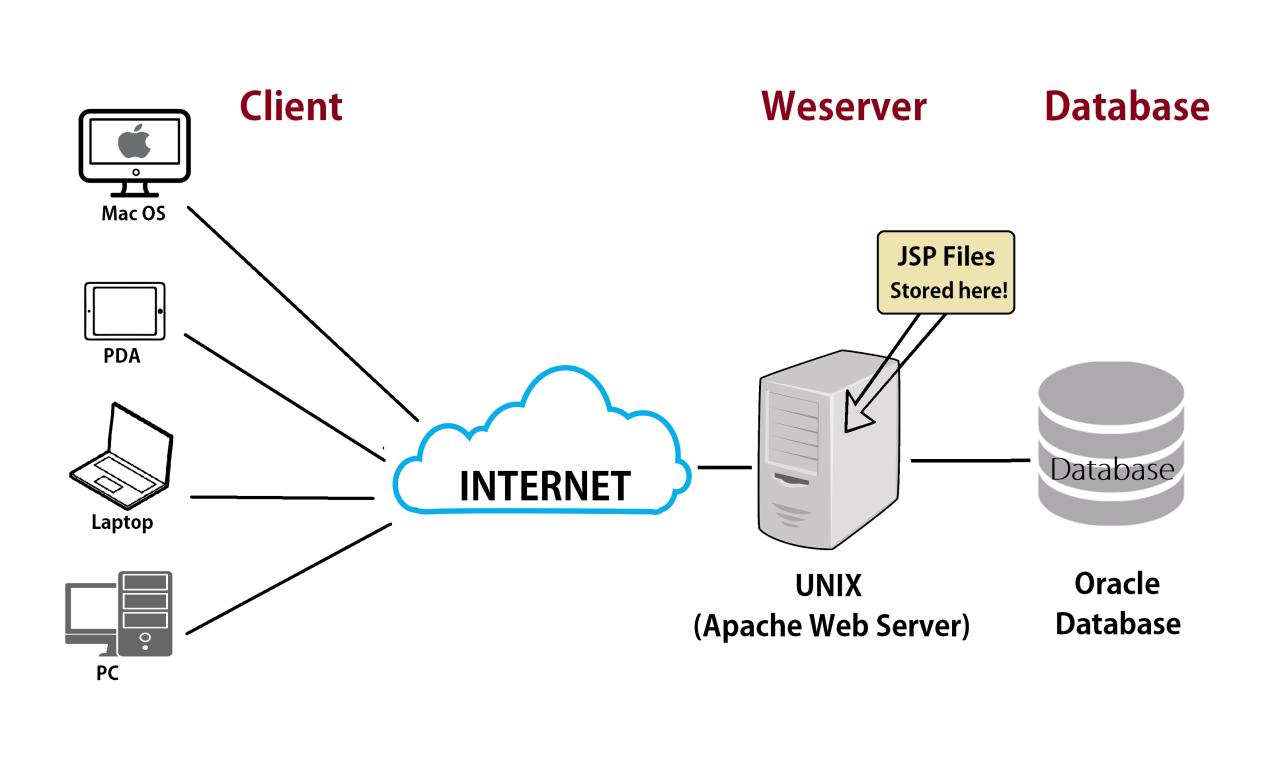
An HTTP server is a program that listens for and responds to requests over the Hypertext Transfer Protocol (HTTP). It acts as the central hub of the web, enabling communication between clients (like web browsers) and web servers.
Role of an HTTP Server
HTTP servers play a crucial role in the functioning of the web. They handle incoming requests from clients, process them, and send back responses containing the requested data. This data can include web pages, images, videos, or other files. The server also manages resources like files and databases, ensuring their availability and security.
HTTP Requests and Responses
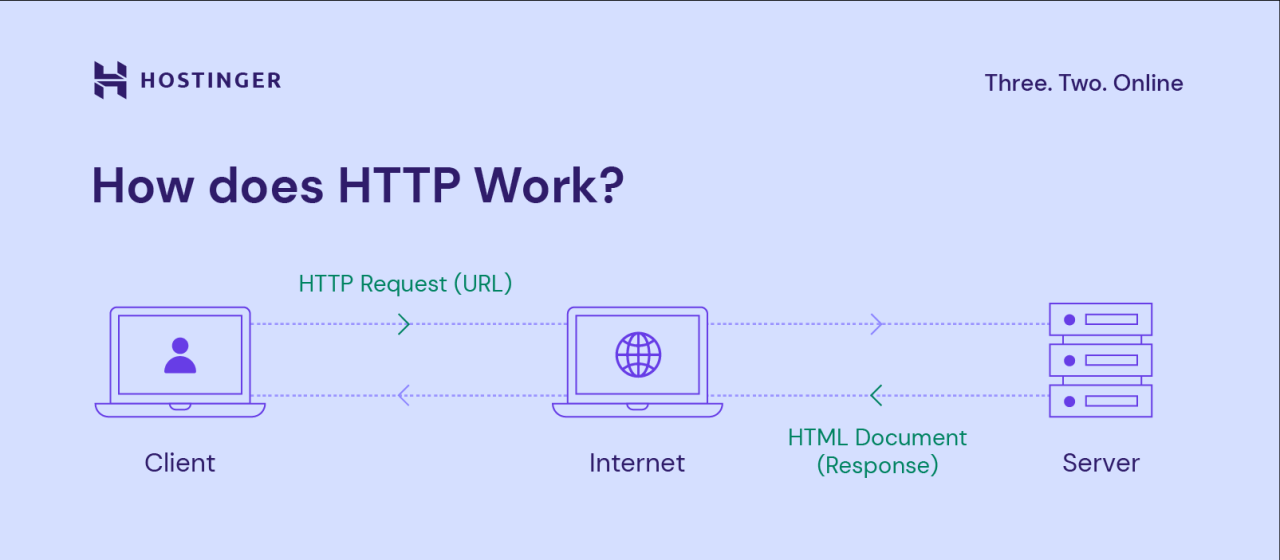
HTTP communication is based on a client-server model. A client sends a request to the server, which then processes the request and sends back a response.
- Request: A client sends a request to the server, specifying the desired resource and the action to be performed. The request includes information such as the method (e.g., GET, POST), the URL of the resource, and the headers containing additional details.
- Response: The server processes the request and sends back a response to the client. The response includes a status code indicating the success or failure of the request, the headers containing additional information, and the requested data.
Architecture of an HTTP Server
An HTTP server typically follows a layered architecture, consisting of multiple components working together to handle requests and responses.
- Connection Handling: This layer establishes and manages connections between the server and clients.
- Request Parsing: This layer receives incoming requests and parses them into their constituent parts, such as the method, URL, and headers.
- Resource Handling: This layer retrieves the requested resources from the server’s storage, such as files or databases.
- Response Generation: This layer generates the response, including the status code, headers, and the requested data.
- Response Sending: This layer sends the generated response back to the client.
HTTP Server Security
HTTP servers are critical components of the internet, handling the transfer of data between clients and web applications. However, they are also vulnerable to various security threats that can compromise the confidentiality, integrity, and availability of data. This section will discuss common security threats to HTTP servers and how to implement security measures to mitigate these risks.
Firewall Rules
Firewalls are essential security tools that act as a barrier between the HTTP server and the external network. They analyze incoming and outgoing network traffic and block unauthorized access based on predefined rules.
- IP Address Blocking: Restrict access to the server from specific IP addresses or IP address ranges. This can be used to block known malicious IP addresses or to limit access to specific regions.
- Port Blocking: Block access to specific ports on the server. For example, you can block access to port 80 (HTTP) and 443 (HTTPS) from untrusted sources. This prevents attackers from accessing the server through known vulnerabilities in HTTP or HTTPS protocols.
- Protocol Filtering: Filter traffic based on the protocol being used. For example, you can block traffic from protocols that are known to be used for malicious activities, such as Telnet or FTP.
Access Control
Access control mechanisms restrict access to specific resources on the HTTP server based on user identity or permissions. This helps to prevent unauthorized users from accessing sensitive data or performing actions that they are not authorized to do.
- User Authentication: Implement user authentication mechanisms to verify the identity of users attempting to access the server. This can be done using username and password combinations, multi-factor authentication, or single sign-on (SSO) solutions.
- Role-Based Access Control (RBAC): Assign roles to users, and each role has specific permissions to access resources. For example, administrators might have full access to all resources, while regular users might only have access to specific pages or data.
- Authorization: Once a user is authenticated, verify their permissions to access specific resources. This can be done using access control lists (ACLs) or other authorization mechanisms.
Input Validation
Input validation is a critical security measure that prevents attackers from injecting malicious code or data into the HTTP server. This can be done by validating user input against predefined rules and sanitizing it to remove any potentially harmful characters.
- Data Type Validation: Ensure that user input is of the correct data type, such as integers, strings, or dates. This prevents attackers from injecting malicious code disguised as data.
- Length Validation: Limit the length of user input to prevent attackers from injecting long strings that could cause buffer overflows or other vulnerabilities.
- Character Validation: Restrict the characters that are allowed in user input. This can help to prevent attackers from injecting special characters or HTML tags that could be used to bypass security measures.
- Sanitization: Remove or escape any potentially harmful characters from user input before processing it. This ensures that the input is safe to use and cannot be used to execute malicious code.
HTTP Server Monitoring and Troubleshooting
Keeping a close eye on your HTTP server’s health is crucial for ensuring its smooth operation and preventing potential issues from impacting your website or application. Monitoring allows you to identify and address problems proactively, minimizing downtime and maintaining a positive user experience.
Tools and Techniques for HTTP Server Monitoring
Monitoring your HTTP server’s performance involves tracking key metrics and using tools to analyze them.
Here are some common tools and techniques used for HTTP server monitoring:
- System Monitoring Tools: Tools like Nagios, Zabbix, and Prometheus provide comprehensive system monitoring capabilities. They can track various metrics such as CPU usage, memory consumption, disk space, and network traffic. These tools often offer customizable dashboards for visualizing performance trends and alerting you to potential issues.
- Web Server Monitoring Tools: Tools specifically designed for web server monitoring, like Apache Status, provide insights into web server performance. They can track metrics like the number of active connections, request processing time, and error rates.
- Log Analysis: Analyzing server logs is essential for identifying errors, security threats, and performance bottlenecks. Log analysis tools like Splunk, Graylog, and ELK (Elasticsearch, Logstash, and Kibana) help you parse and analyze log data to gain valuable insights.
- Performance Testing Tools: Tools like Apache JMeter and LoadRunner allow you to simulate real-world traffic loads on your web server. This helps identify performance bottlenecks and ensure your server can handle expected traffic levels.
Troubleshooting Scenarios and Solutions
Understanding common HTTP server issues and how to troubleshoot them is essential for maintaining a healthy and responsive server.
Here are some common troubleshooting scenarios and solutions:
- Slow Website Load Times: If your website is loading slowly, several factors could be contributing. You can start by checking server performance metrics, such as CPU usage, memory consumption, and disk I/O. If these metrics are high, you may need to consider upgrading your server hardware or optimizing your website code for better performance.
- High Error Rates: Increased error rates in your server logs can indicate issues with your website code, database, or server configuration. Analyze the error messages to identify the root cause. For example, “404 Not Found” errors suggest missing files or incorrect URLs.
- High CPU Usage: If your server’s CPU usage is consistently high, it can impact performance. Identify the processes consuming the most CPU resources. This could be a result of a resource-intensive website script, a malicious attack, or a poorly configured service.
- Website Downtime: If your website is down, you need to quickly diagnose the problem. Check your server logs for error messages. If the server is not responding, you may need to contact your hosting provider or check for network connectivity issues.
Conclusion
Understanding HTTP servers unlocks a deeper appreciation for the internet’s magic. Whether you’re a curious user or a budding developer, comprehending the inner workings of these powerful machines empowers you to navigate the digital landscape with confidence. As we delve further into the world of HTTP servers, we discover the intricacies of their architecture, configuration, and security measures, revealing the fascinating mechanisms that power the web as we know it.