Proxy Site 1, the unsung hero of internet freedom, empowers users to navigate the web with enhanced privacy and access to blocked content. This intricate web of servers acts as an intermediary, routing your requests and masking your identity, allowing you to browse freely, bypassing geographical limitations and enhancing your online security.
Understanding how proxy sites work is crucial for navigating the digital landscape effectively. This article delves into the technical intricacies, exploring the various types of proxy sites, their legitimate uses, and the potential security and privacy concerns associated with their usage.
Future Trends in Proxy Site Technology
Proxy sites have become increasingly popular in recent years, offering users a way to access blocked content, enhance privacy, and circumvent censorship. As technology continues to evolve, proxy site technology is also undergoing significant transformations, with emerging trends and advancements shaping the future of this domain.
Emerging Trends and Advancements in Proxy Site Technology, Proxy site 1
The landscape of proxy site technology is constantly evolving, driven by advancements in network protocols, encryption techniques, and user demand for enhanced privacy and security. Some notable emerging trends include:
- Advanced Encryption Techniques: Proxy sites are increasingly adopting sophisticated encryption algorithms, such as TLS 1.3 and end-to-end encryption, to safeguard user data and communications. This enhances user privacy and makes it more difficult for third parties to intercept or monitor traffic.
- Decentralized Proxy Networks: Decentralized proxy networks, such as Tor and I2P, are gaining traction. These networks distribute traffic across multiple nodes, making it more difficult to identify and track individual users. This approach enhances privacy and anonymity, making it challenging for authorities to block or monitor access.
- AI-Powered Proxy Optimization: Artificial intelligence (AI) is being integrated into proxy site technology to optimize performance and efficiency. AI algorithms can analyze traffic patterns, identify bottlenecks, and dynamically route traffic through the most efficient proxy servers. This results in faster loading times and a smoother user experience.
- Proxy Site Integration with Web Browsers: Some web browsers are integrating built-in proxy features, providing users with a more seamless and convenient way to access proxy services. This integration simplifies the process of accessing blocked content or enhancing privacy without the need for external extensions or add-ons.
Potential Future Applications and Use Cases of Proxy Sites
Proxy sites have the potential to be utilized in a wide range of applications beyond simply accessing blocked content. Future use cases may include:
- Enhanced Online Privacy and Security: Proxy sites can be used to protect user privacy and security by masking their IP addresses and encrypting their online activities. This is particularly relevant in situations where users are concerned about data breaches or surveillance.
- Circumventing Censorship and Geo-Restrictions: Proxy sites can be used to access content that is blocked in certain geographical locations or restricted by government censorship. This allows users to access information and services that would otherwise be inaccessible.
- Testing and Debugging Websites: Developers and testers can use proxy sites to simulate different network conditions and geographic locations, allowing them to test and debug websites in various environments. This can help identify and resolve issues related to website performance or accessibility.
- Accessing Content from Different Regions: Proxy sites can be used to access content from different regions of the world, allowing users to explore diverse cultural perspectives and access region-specific services.
- Business and Enterprise Applications: Proxy sites can be used by businesses to access geographically restricted resources, such as online databases or cloud services. They can also be used to enhance security and privacy for sensitive data transmission.
Impact of Evolving Internet Regulations and Security Measures on Proxy Site Usage
The evolving landscape of internet regulations and security measures can have a significant impact on proxy site usage. Governments and internet service providers are increasingly implementing measures to restrict access to proxy sites, such as blocking specific IP addresses or using deep packet inspection techniques to identify and filter proxy traffic.
“The ongoing battle between proxy site providers and authorities is a constant arms race, with each side developing new tactics to outmaneuver the other.”
These measures can make it more challenging for users to access proxy sites and may lead to increased use of more sophisticated and decentralized proxy networks, such as Tor or I2P, which are more difficult to block.
Ultimate Conclusion: Proxy Site 1
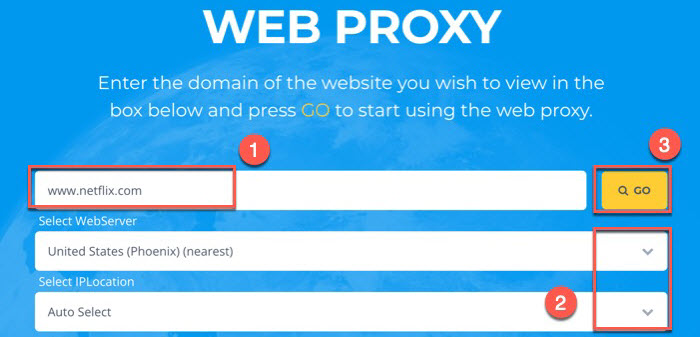
As the digital world evolves, proxy sites remain a valuable tool for maintaining online privacy and accessing information freely. While they offer numerous advantages, understanding the potential risks and adopting best practices is crucial for maximizing their benefits and minimizing vulnerabilities. By carefully selecting and utilizing proxy sites, you can navigate the internet with greater control and confidence, shaping your online experience to meet your specific needs.