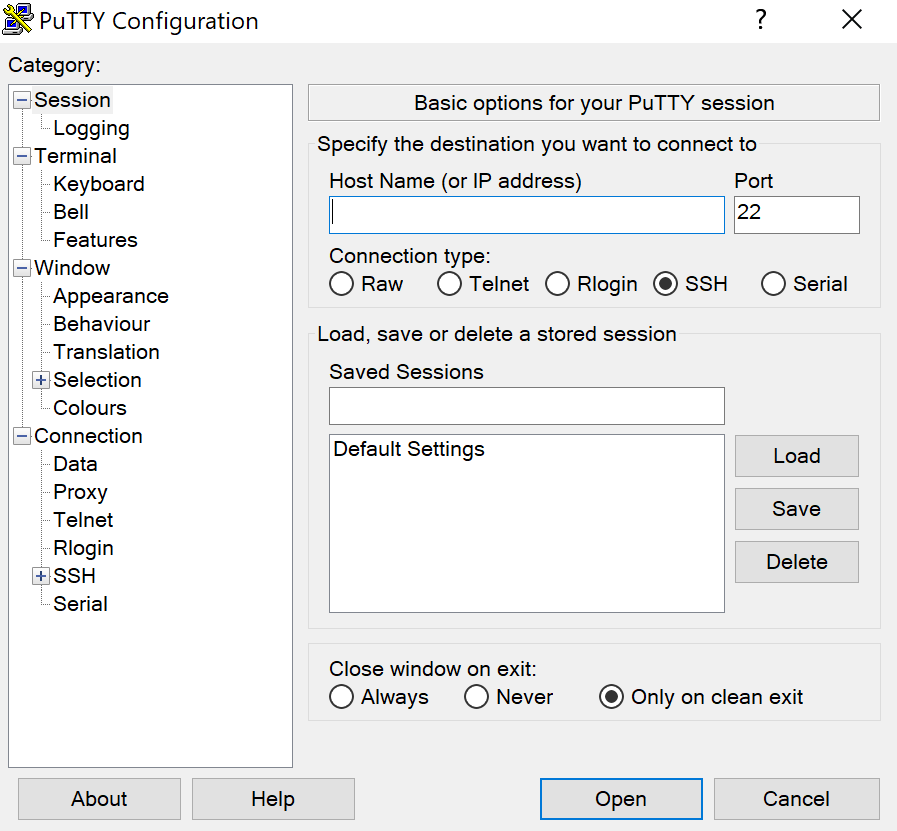
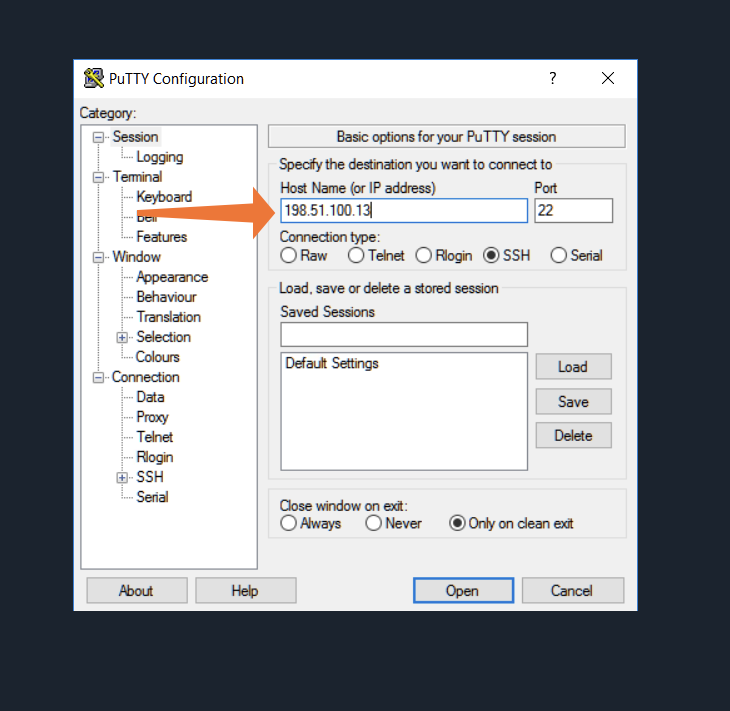
PuTTY SSH, a widely used SSH client, opens the door to secure remote access, allowing you to connect to servers and manage them from anywhere. This powerful tool offers a user-friendly interface, enabling seamless communication and control over remote systems.
Whether you’re a seasoned system administrator or a web developer, PuTTY SSH provides the essential tools for managing your infrastructure, executing commands, transferring files, and even accessing remote applications.
What is PuTTY SSH?
PuTTY SSH is a free and open-source terminal emulator and SSH client that enables secure remote access to computer systems. It allows users to connect to remote servers and execute commands as if they were directly on the server.
PuTTY SSH plays a crucial role in securing remote access by encrypting all data transmitted between the client and the server. This ensures that sensitive information, such as passwords and other confidential data, remains protected during transmission.
Core Functionalities
PuTTY SSH provides a range of functionalities to facilitate secure remote access.
- Secure Shell (SSH) Protocol: PuTTY SSH utilizes the SSH protocol, which provides secure communication channels between client and server. This protocol encrypts all data exchanged, preventing unauthorized access and eavesdropping.
- Terminal Emulation: PuTTY emulates various terminal types, allowing users to interact with remote servers using familiar command-line interfaces.
- File Transfer: PuTTY supports file transfer protocols like SFTP and SCP, enabling users to securely transfer files between their local machine and the remote server.
- Port Forwarding: PuTTY allows for port forwarding, which redirects network traffic from one port on the client machine to another port on the remote server. This functionality is useful for accessing services running on the remote server that are not directly accessible from the client.
- Tunneling: PuTTY can create secure tunnels for accessing resources on a private network from a public network. This is useful for securely accessing resources within a company’s internal network from a home computer.
PuTTY SSH Features
PuTTY SSH offers a robust set of features designed to facilitate secure remote access and management of servers. These features empower users to perform various tasks, including executing commands, transferring files, and establishing secure connections.
Terminal Emulation
PuTTY SSH provides terminal emulation, allowing users to interact with remote servers as if they were directly connected to the console. This feature is essential for managing remote servers, running commands, and troubleshooting issues. PuTTY supports various terminal emulators, including xterm, vt100, and ANSI, ensuring compatibility with different server configurations.
File Transfer
PuTTY SSH includes a built-in file transfer protocol (SFTP) client, enabling users to transfer files securely between their local computer and remote servers. This feature is crucial for deploying applications, updating files, and managing server content. SFTP utilizes encryption to protect data during transmission, ensuring secure file transfers.
Port Forwarding
PuTTY SSH supports port forwarding, a mechanism that allows users to establish secure connections to remote services through an SSH tunnel. This feature is valuable for accessing services that are not accessible directly from the internet, such as internal databases or web servers. PuTTY offers two types of port forwarding:
- Local Port Forwarding: Redirects traffic from a local port on the user’s computer to a remote port on the server.
- Remote Port Forwarding: Redirects traffic from a remote port on the server to a local port on the user’s computer.
Advanced PuTTY SSH Techniques
PuTTY SSH offers several advanced features that enhance its capabilities for complex remote access scenarios. These features allow users to perform specialized tasks, improve security, and streamline workflows. This section delves into some of the most notable advanced techniques, exploring their functionalities, practical applications, and considerations.
SSH Tunneling
SSH tunneling creates a secure channel within an existing SSH connection, allowing the transfer of data between two points over an encrypted tunnel. This technique is beneficial for various purposes, including:
- Secure Access to Internal Networks: Tunneling allows users to access resources on a private network from a remote location. By establishing an SSH tunnel from the client to a server within the private network, the user can access resources on the internal network as if they were physically connected.
- Secure Web Browsing: Tunneling can be used to browse the internet securely through a remote server. By creating an SSH tunnel to a server, the user’s web traffic is routed through the tunnel, making it appear as if the user is accessing the internet from the server’s location.
- Port Forwarding: SSH tunneling allows for port forwarding, redirecting traffic from a specific port on the client machine to a different port on the server. This is useful for accessing services that are not directly accessible through SSH, such as databases or web servers.
Example: To access a web server on an internal network, a user can establish an SSH tunnel to a server within the network and configure the tunnel to forward traffic from port 80 on the client machine to port 80 on the web server. The user can then access the web server through their web browser by accessing the server’s IP address or domain name on port 80.
SSH Multiplexing
SSH multiplexing allows users to share a single SSH connection for multiple sessions. This is particularly useful when working with multiple remote servers or when connecting to a server that requires frequent logins.
- Reduced Connection Overhead: By sharing a single connection, multiplexing minimizes the overhead associated with establishing multiple connections. This improves performance and reduces the time required to connect to multiple servers.
- Simplified Session Management: Multiplexing simplifies session management by allowing users to manage multiple sessions through a single connection. Users can easily switch between sessions without reconnecting to the server.
Example: A user can establish an SSH multiplexing connection to a server and open multiple terminal sessions within that connection. Each session can be used to access a different directory or run a different command.
SSH Scripting
SSH scripting allows users to automate repetitive SSH tasks, such as connecting to multiple servers, executing commands, and transferring files. This can significantly streamline workflows and reduce manual effort.
- Automation: SSH scripting automates tasks, eliminating the need for manual intervention. This can save time and improve efficiency.
- Consistency: Scripts ensure that tasks are performed consistently, reducing the risk of errors.
- Remote Management: Scripts can be used to manage remote servers without requiring physical access.
Example: A script can be created to connect to multiple servers, execute a specific command on each server, and then collect the output from each command.
PuTTY SSH in the Real World
PuTTY SSH is not just a technical tool; it’s a vital component of modern workflows across various fields. From web development to system administration and data analysis, PuTTY SSH empowers users to connect, manage, and interact with remote systems seamlessly.
Real-World Applications, Putty ssh
PuTTY SSH plays a crucial role in various real-world scenarios, enabling remote access and control over computer systems.
- Web Development: Developers use PuTTY SSH to access and manage web servers, deploy websites, and troubleshoot issues remotely. They can use it to configure web server settings, install software, and manage files, all without being physically present at the server location.
- System Administration: System administrators rely on PuTTY SSH to monitor and manage servers, update software, configure security settings, and troubleshoot system problems. They can remotely access and control servers, ensuring smooth operation and efficient resource utilization.
- Data Analysis: Data analysts use PuTTY SSH to access and manipulate data stored on remote servers. They can transfer large datasets, run analysis scripts, and visualize data, facilitating efficient data exploration and analysis.
Remote Work and Collaboration
PuTTY SSH plays a vital role in enabling remote work and collaboration, fostering a flexible and connected work environment.
- Remote Access: PuTTY SSH allows employees to securely access their work computers from anywhere with an internet connection, enabling them to work remotely without compromising security.
- Collaboration: PuTTY SSH facilitates collaboration among team members working on projects involving remote servers. They can share files, access data, and work together seamlessly, regardless of their physical location.
- Increased Productivity: Remote access and collaboration enabled by PuTTY SSH improve productivity by allowing employees to work from anywhere, eliminating the need for physical office space and reducing commuting time.
End of Discussion
Mastering PuTTY SSH empowers you with the ability to interact with remote systems securely and efficiently. By understanding its features, configurations, and best practices, you can unlock a world of possibilities, from managing your own servers to collaborating on projects remotely.