RODC, or Read-Only Domain Controller, sets the stage for this exploration, offering readers a comprehensive understanding of this vital component within Active Directory environments. This guide delves into the intricacies of RODCs, exploring their purpose, functionality, and deployment considerations. From security implications to practical use cases, we aim to provide a clear and concise overview of this powerful tool.
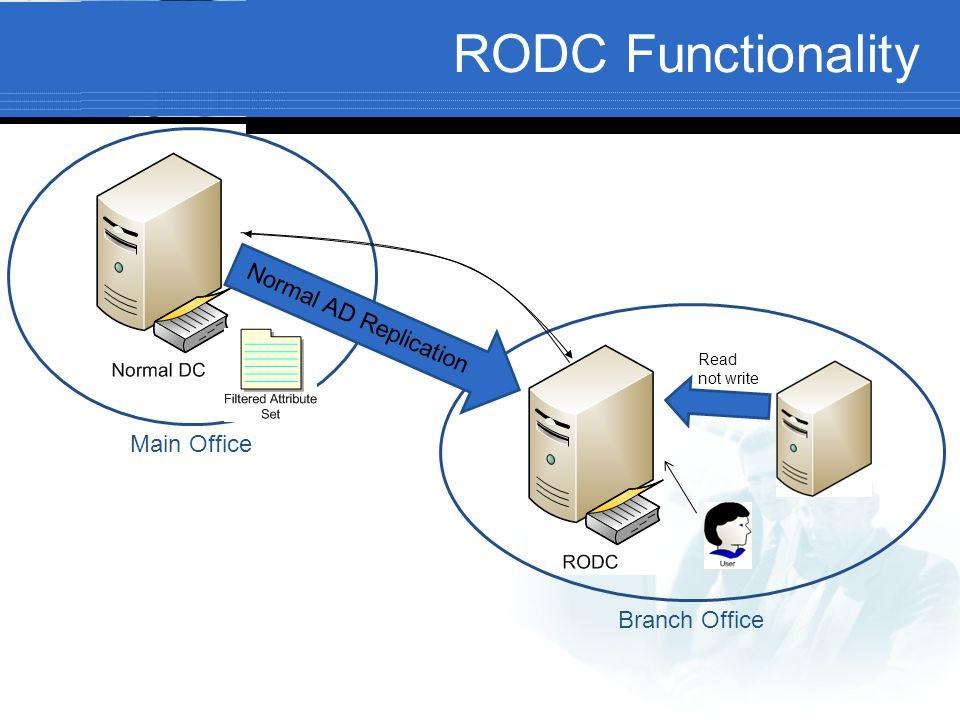
Imagine a distributed network with remote offices or branch locations needing to authenticate users and access resources securely. RODCs step in to provide a local, read-only copy of Active Directory data, enabling seamless user authentication and access to resources, even with limited connectivity to the main domain. This approach not only enhances security by minimizing the potential for unauthorized access to sensitive data but also optimizes performance by reducing reliance on centralized resources.
What is a RODC?
A Read-Only Domain Controller (RODC) is a special type of domain controller in a Windows Active Directory environment that provides read-only access to the directory service. Unlike a standard domain controller (DC), an RODC cannot perform write operations, such as creating or modifying user accounts, groups, or other directory objects.
The primary purpose of an RODC is to extend Active Directory services to remote locations or branch offices where network connectivity to the main domain controllers is limited or unreliable. By deploying an RODC in such locations, users and computers can still authenticate with the domain and access resources such as shared folders and printers, even when the connection to the main DCs is down.
Key Features and Functionalities of an RODC
An RODC offers several key features and functionalities, including:
- Read-only access to the directory service: RODCs only allow read operations on the directory service, preventing unauthorized modifications or deletions of data. This enhances security by limiting the potential impact of malicious attacks or accidental data corruption.
- Offline authentication: Users and computers can authenticate with an RODC even when the connection to the main DCs is unavailable. This enables continued access to domain resources and ensures business continuity in case of network outages.
- Reduced replication traffic: RODCs replicate only a subset of the directory data from the main DCs, reducing the amount of replication traffic on the network. This can improve network performance and reduce bandwidth consumption, especially in remote locations with limited connectivity.
- Improved security: RODCs can be configured with additional security measures, such as requiring a specific password for administrative tasks. This further enhances security by limiting access to critical functions.
- Simplified deployment: RODCs are relatively easy to deploy and manage compared to standard DCs. They require less disk space and have a smaller footprint, making them suitable for resource-constrained environments.
RODC vs. Read-Only Domain Controller (RODC)
The terms “RODC” and “Read-Only Domain Controller (RODC)” are often used interchangeably, but they refer to the same type of Active Directory domain controller. However, there are subtle differences in their usage and context that are important to understand.
Terminology and Usage
- RODC: This is the acronym commonly used to refer to Read-Only Domain Controllers. It’s a concise and widely recognized abbreviation within the Active Directory community.
- Read-Only Domain Controller (RODC): This is the full, descriptive term for the type of domain controller. It explicitly states the controller’s primary function, which is to provide read-only access to Active Directory data.
While both terms are accurate, the choice between them depends on the specific context and audience. In technical discussions or documentation, the acronym “RODC” is generally preferred for brevity. However, when explaining the concept to non-technical audiences, using the full term “Read-Only Domain Controller” might be more appropriate.
Functionality and Limitations
RODCs are designed to provide read-only access to Active Directory data. They are primarily used in scenarios where:
- Limited connectivity to the main domain: RODCs are ideal for branch offices or remote locations with intermittent or unreliable network connections. They can cache a subset of the Active Directory data locally, enabling users to authenticate and access resources even when the connection to the main domain is down.
- Security concerns: RODCs can be configured to restrict write operations, reducing the risk of unauthorized modifications to Active Directory data. This is particularly beneficial in environments with sensitive data or where there are concerns about security breaches.
However, RODCs have limitations:
- Limited write operations: RODCs cannot perform write operations to the Active Directory database. This means that tasks such as creating new users, groups, or computers, or modifying existing objects, must be performed on a writable domain controller.
- Limited replication: RODCs replicate only a subset of the Active Directory data from a writable domain controller. This means that they may not have the most up-to-date information, especially for frequently changing objects.
It’s important to understand that the term “Read-Only Domain Controller” is not a technical term within Active Directory. It’s a general description of a type of domain controller. The specific functionality and limitations of a domain controller are determined by its configuration and role within the Active Directory environment.
Specific Scenarios
Here are some specific scenarios where RODCs are commonly used:
- Branch offices: RODCs are deployed in branch offices to provide local authentication and resource access for users, even when the connection to the main domain is down. This minimizes downtime and improves user productivity.
- Remote locations: RODCs are ideal for remote locations with limited connectivity. They can cache a subset of the Active Directory data locally, enabling users to authenticate and access resources without relying on a constant connection to the main domain.
- High-security environments: RODCs can be configured to restrict write operations, reducing the risk of unauthorized modifications to Active Directory data. This is particularly beneficial in environments with sensitive data or where there are concerns about security breaches.
RODC Deployment and Configuration
Deploying and configuring a RODC involves several steps, requiring specific permissions and prerequisites for successful implementation. The process of replicating data from a primary domain controller to a RODC is crucial for maintaining consistency and ensuring functionality.
Permissions and Prerequisites
Deploying a RODC requires specific permissions and prerequisites. These ensure that the deployment process is secure and that the RODC can function correctly within the domain environment.
- Domain Admin Privileges: The user deploying the RODC must have Domain Admin privileges to create and configure the RODC. These privileges grant access to critical domain resources, enabling the necessary configuration changes.
- Active Directory Schema Extension: The Active Directory schema must be extended to support RODCs. This extension is usually included with the Windows Server operating system but may need to be manually installed in some cases. The schema extension allows the domain to recognize and manage RODCs.
- Existing Domain Controller: A primary domain controller (PDC) must already exist in the domain before deploying an RODC. The PDC serves as the primary source of data for the RODC, providing replication and synchronization of critical information.
- Windows Server Operating System: The RODC must be running a supported version of the Windows Server operating system. This ensures compatibility with Active Directory and other domain services.
- Network Connectivity: The RODC must be connected to the domain network and able to communicate with the PDC. This connectivity is essential for replication and synchronization of data.
Deployment Steps
Deploying an RODC involves a series of steps, ensuring proper integration and functionality within the domain environment.
- Prepare the Server: Install the required operating system and configure the server’s basic settings, such as hostname and IP address. Ensure that the server meets the minimum hardware requirements for an RODC.
- Promote the Server to RODC: Use the “Active Directory Domain Services Installation Wizard” to promote the server to an RODC. This involves selecting the RODC role during the installation process and specifying the PDC from which the RODC will replicate data.
- Configure Replication Settings: Specify the replication schedule and other settings to control how data is replicated from the PDC to the RODC. These settings determine the frequency and scope of replication, balancing data consistency with network bandwidth usage.
- Configure User Account Restrictions: Define the restrictions for user account management on the RODC. This includes specifying which user accounts can be created, modified, or deleted on the RODC. This restriction enhances security by limiting access to sensitive user account information.
- Configure Group Policy: Configure the group policy settings for the RODC. This allows for customizing user and computer settings specific to the RODC. This configuration ensures that the RODC enforces the desired security policies and user experience.
- Test and Monitor: After deployment, thoroughly test the RODC to ensure its functionality and data consistency. Regularly monitor the RODC’s performance and replication status to identify and resolve any issues.
Data Replication from PDC to RODC
Replication of data from the PDC to the RODC is crucial for maintaining consistency and functionality. The process involves the following steps:
- Initial Replication: When an RODC is first deployed, it performs an initial replication from the PDC, obtaining a full copy of the domain data. This initial replication establishes the RODC’s initial state and ensures that it has a complete set of domain information.
- Incremental Replication: After the initial replication, the RODC performs incremental replication, receiving only the changes made to the domain data since the last replication. This process ensures that the RODC stays synchronized with the PDC without replicating the entire domain data every time.
- Replication Schedule: The replication schedule determines the frequency of replication. This schedule can be configured to balance data consistency with network bandwidth usage. A more frequent replication schedule ensures data consistency but may consume more network bandwidth, while a less frequent schedule conserves bandwidth but may result in slightly delayed data updates.
RODC Use Cases
RODCs are valuable tools in domain environments, offering advantages in specific situations. They can be deployed to enhance security and improve performance in various scenarios.
Branch Office Deployment
RODCs are ideal for branch offices, where network connectivity to the main domain might be limited or unreliable. They offer several advantages:
- Reduced Bandwidth Consumption: RODCs only replicate a subset of the Active Directory database, significantly reducing the amount of data transferred over the network. This is crucial for branch offices with limited bandwidth.
- Improved Performance: With local authentication, user logins and other operations are handled locally, reducing the load on the main domain controllers and improving user experience.
- Enhanced Security: RODCs store only a limited amount of sensitive data, making them less attractive targets for attackers. They also support read-only access, preventing unauthorized modifications to the Active Directory database.
Remote User Authentication
RODCs can be deployed in environments where users work remotely or have limited access to the corporate network.
- Offline Authentication: RODCs allow users to authenticate even when disconnected from the main domain, ensuring uninterrupted access to critical resources.
- Enhanced Security: RODCs reduce the risk of unauthorized access by limiting the amount of sensitive data stored on the server.
- Reduced Network Load: Authentication requests are handled locally, reducing the load on the main domain controllers and improving overall network performance.
Disaster Recovery
RODCs can be deployed as part of a disaster recovery strategy to ensure business continuity in the event of a main domain controller failure.
- Reduced Downtime: RODCs can continue to provide authentication and authorization services even if the main domain controllers are unavailable, minimizing downtime and disruptions.
- Enhanced Resilience: RODCs provide a backup authentication mechanism, ensuring that users can still access critical resources even in the event of a disaster.
- Cost-Effective Solution: RODCs can be deployed at a lower cost compared to replicating the entire Active Directory database, making them a cost-effective disaster recovery solution.
Data Security
RODCs enhance data security by limiting the amount of sensitive data stored on the server.
- Reduced Attack Surface: RODCs store only a subset of the Active Directory database, making them less attractive targets for attackers.
- Read-Only Access: RODCs provide read-only access to the Active Directory database, preventing unauthorized modifications.
- Improved Compliance: RODCs can help organizations meet compliance requirements by limiting the amount of sensitive data stored on the server.
RODC Limitations and Considerations
While RODCs offer significant advantages for distributed environments, they come with certain limitations that must be carefully considered. These limitations can impact user authentication, data access, and overall security.
Impact on User Authentication and Data Access
RODCs have limitations that affect user authentication and data access, primarily due to their offline nature and reduced functionality.
- Limited Authentication Capabilities: RODCs cannot authenticate users who have never authenticated against a writable domain controller. This limitation arises because RODCs do not store the full user account database. Users who need to access resources on the RODC for the first time must authenticate against a writable domain controller to establish their credentials in the RODC’s local cache.
- Limited Password Changes and Resets: RODCs cannot process password changes or resets for users who have never authenticated against a writable domain controller. Users attempting to change or reset their passwords must authenticate against a writable domain controller. This limitation is due to the RODC’s limited access to the user account database.
- Restricted Group Policy Processing: RODCs cannot process all Group Policy settings, particularly those related to user accounts, security, and password policies. This limitation is due to the RODC’s limited access to the full Group Policy database. Some Group Policy settings might not be applied consistently across all RODCs, potentially affecting user experience and security.
Mitigating Potential Challenges
Understanding and mitigating potential challenges associated with RODC deployment is crucial for ensuring optimal performance and security.
- Careful Planning and Design: Before deploying RODCs, carefully consider the specific requirements of your environment. Identify the locations where RODCs are needed and assess the potential impact of their limitations on user authentication, data access, and security.
- Regular Synchronization with Writable Domain Controllers: Ensure that RODCs are regularly synchronized with writable domain controllers to keep their local caches up-to-date. This synchronization process is crucial for maintaining accurate user account information, password policies, and other critical data.
- Understanding and Managing Group Policy Settings: Carefully select and manage Group Policy settings that will be applied through RODCs. Ensure that the chosen settings are compatible with the RODC’s limitations and that they do not compromise user authentication or security.
- Implement Strong Password Policies: Implement robust password policies to minimize the risk of unauthorized access and data breaches. This is particularly important in environments where RODCs are used, as they have limited authentication capabilities.
- Use a Centralized Authentication Server: Consider using a centralized authentication server, such as a writable domain controller, to handle user authentication and password management for critical applications. This can mitigate the impact of RODC limitations on security and performance.
RODC and Active Directory Replication
RODCs play a crucial role in Active Directory (AD) environments, providing read-only access to critical information for users and devices in remote locations. However, the way RODCs replicate data from primary domain controllers (PDCs) is different from traditional replication processes. This section delves into the specifics of RODC replication, exploring its impact on performance and security, and highlighting factors that influence replication frequency and data consistency.
Replication Process
RODCs do not participate in the full replication process like traditional domain controllers. They receive a snapshot of the AD database from a PDC at specific intervals. This snapshot includes a subset of the data, primarily focusing on objects relevant to user authentication and group memberships. RODCs don’t replicate all the data from a PDC, and they don’t replicate changes made on other RODCs.
Replication Impact on Performance and Security, Rodc
Performance
- Reduced Replication Traffic: RODCs only receive a snapshot of the data, resulting in significantly less replication traffic compared to traditional domain controllers. This reduces network bandwidth usage and improves overall performance, especially in remote locations with limited bandwidth.
- Faster Authentication: RODCs store a subset of the AD database, allowing for faster authentication and authorization requests from users and devices located in the same location. This improves user experience and reduces network latency.
Security
- Enhanced Security: RODCs don’t participate in the full replication process, making them less vulnerable to attacks that target the replication process. They also have limited write access, making them more resistant to malicious modifications.
- Data Integrity: RODCs receive a snapshot of the data, ensuring that the data on the RODC is consistent with the PDC at the time of the snapshot. This helps maintain data integrity and reduces the risk of inconsistencies.
Factors Affecting Replication Frequency and Data Consistency
Several factors influence the frequency of replication and the consistency of data between RODCs and PDCs. These include:
- Replication Schedule: The replication schedule is configured on the PDC and determines how often RODCs receive data updates. The default replication schedule is every 15 minutes, but it can be adjusted based on specific requirements.
- Network Connectivity: The availability and quality of the network connection between the RODC and the PDC significantly impact replication frequency. If the connection is unstable or unreliable, replication may be delayed or fail altogether.
- Data Changes: The volume of changes made to the AD database on the PDC directly affects replication frequency. More frequent changes require more frequent replication to ensure data consistency.
RODC and Password Management
RODCs play a crucial role in securing sensitive data by restricting access to critical resources. This security measure extends to password management, as RODCs handle password changes and resets differently than traditional domain controllers.
Password Changes and Resets
RODCs do not store the full password hash for user accounts. Instead, they store a password change token, which is a unique identifier associated with a user’s password change request. When a user attempts to change their password on an RODC, the RODC sends the password change token to a writeable domain controller (WDC). The WDC processes the password change request, updates the user’s password hash, and then sends a confirmation back to the RODC.
Implications for RODC Security
This approach enhances RODC security by preventing attackers from accessing the password hash directly from the RODC. However, it also presents some challenges:
- Limited Password Reset Functionality: RODCs cannot reset passwords directly. Users must contact a WDC or administrator to reset their passwords. This can be inconvenient for users who need to access resources on the RODC.
- Potential for Denial of Service: If a WDC is unavailable or experiencing network issues, users may be unable to change or reset their passwords on the RODC.
- Increased Complexity: Managing password changes and resets in a RODC environment requires careful planning and configuration to ensure that users can access the resources they need without compromising security.
Password Management Strategies
To mitigate the challenges associated with password management in a RODC environment, consider these strategies:
- Use a Centralized Password Management System: Implement a system that allows users to reset their passwords from any device, regardless of whether they are connected to a RODC or a WDC. This can improve user convenience and reduce the risk of denial of service attacks.
- Configure RODC Replication Schedules: Ensure that the RODC replicates password changes from WDCs frequently to minimize the impact of WDC unavailability. This helps to ensure that users can access resources on the RODC even if the WDC is temporarily offline.
- Educate Users: Train users on the limitations of password management in a RODC environment and how to handle password change requests. This can help to prevent frustration and ensure that users are aware of the proper procedures.
RODC and Future Directions
The Read-Only Domain Controller (RODC) has evolved significantly since its inception, playing a crucial role in securing and extending Active Directory deployments. As technology continues to advance, the future of RODCs holds promising developments and expanded applications.
Potential Advancements and New Features
The ongoing evolution of RODC technology presents exciting possibilities for enhancing functionality and addressing emerging security challenges. Potential advancements include:
- Enhanced Security Measures: Implementing advanced security features like hardware-based security modules (HSMs) for key storage and encryption could further strengthen RODC security, making them even more resistant to attacks.
- Improved Performance and Scalability: Optimizations to replication and authentication processes could lead to improved performance and scalability, enabling RODCs to handle larger user bases and demanding workloads more effectively.
- Cloud Integration: Integration with cloud-based services, such as Azure Active Directory, could enable RODCs to leverage cloud infrastructure for enhanced management, scalability, and disaster recovery capabilities.
- Support for Modern Authentication Protocols: Integrating support for modern authentication protocols, like OAuth 2.0 and OpenID Connect, would enhance security and interoperability with cloud-based applications.
- Advanced Auditing and Monitoring: Enhanced auditing and monitoring capabilities could provide more granular insights into RODC activity, aiding in security incident detection and response.
Role of RODCs in Modern Active Directory Deployments
In contemporary Active Directory deployments, RODCs are likely to play a more prominent role due to the increasing demand for distributed, secure, and highly available environments. Their advantages, such as reduced replication traffic and enhanced security, make them well-suited for:
- Branch Office Deployments: RODCs remain a vital component for securing and managing Active Directory resources in remote branch offices, minimizing replication traffic and reducing the attack surface.
- Hybrid Cloud Environments: As organizations adopt hybrid cloud strategies, RODCs can serve as a bridge between on-premises Active Directory and cloud-based services, enabling seamless integration and user authentication.
- Disaster Recovery and Business Continuity: RODCs can serve as a critical component of disaster recovery plans, ensuring business continuity by providing read-only access to essential Active Directory data in case of an outage.
- Security Hardening: RODCs are increasingly being utilized as part of security hardening strategies, particularly in environments where sensitive data is stored, minimizing the risk of unauthorized access.
Ultimate Conclusion
RODCs are a valuable asset in modern Active Directory environments, offering enhanced security, improved performance, and flexible deployment options. Understanding the nuances of RODCs, from their security implications to their practical use cases, is crucial for network administrators seeking to optimize their domain infrastructure. By implementing and managing RODCs effectively, organizations can ensure seamless user authentication, secure access to resources, and improved overall network performance.




