Secret servers, shrouded in mystery, play a crucial role in protecting sensitive information. They act as digital fortresses, safeguarding critical data from unauthorized access. These servers are often deployed by organizations seeking to secure confidential data, such as financial records, intellectual property, or sensitive personal information.
This exploration delves into the realm of secret servers, examining their purpose, security measures, and the complexities of managing them. We will discuss the various threats they face, the importance of strong authentication, and the intricacies of access control. Furthermore, we will explore legal and ethical considerations, real-world examples, and best practices for maintaining the security and integrity of these hidden digital vaults.
Future Trends in Secret Server Security
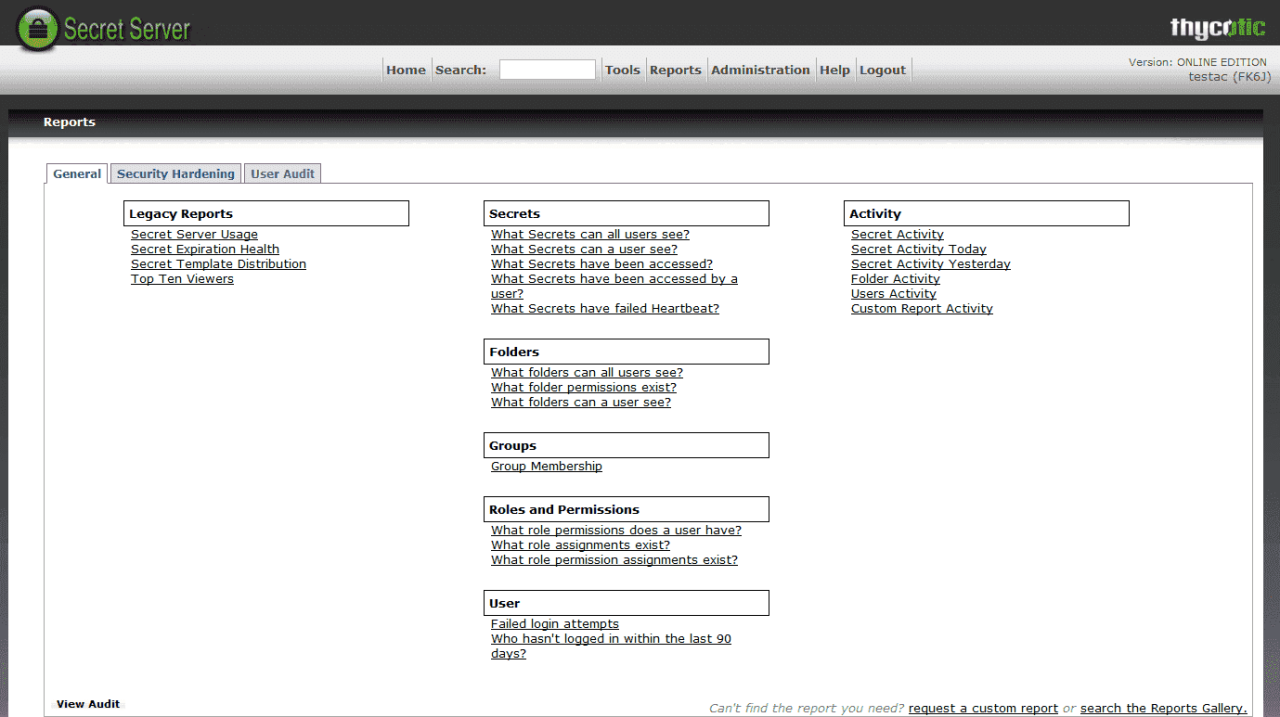
Secret server security is a critical aspect of protecting sensitive data. As technology evolves, so do the threats to this data. It’s essential to stay ahead of these threats by understanding the emerging trends in secret server security and their potential impact on data protection.
Emerging Trends in Secret Server Security
Several trends are shaping the future of secret server security. These trends present both opportunities and challenges for organizations seeking to protect their data.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are being increasingly used to enhance security measures, detect anomalies, and automate security tasks. AI-powered security solutions can analyze vast amounts of data to identify suspicious activity, predict potential threats, and respond in real-time.
- Zero Trust Security: This approach assumes that no user or device can be trusted by default. It requires strong authentication and continuous verification to access sensitive data and resources. Zero trust security models are becoming increasingly popular as organizations seek to reduce their attack surface.
- Cloud-Native Security: As more organizations migrate their applications and data to the cloud, cloud-native security solutions are becoming increasingly important. These solutions are designed to protect cloud environments and ensure the security of data and applications in the cloud.
- DevSecOps: This approach integrates security into the development and operations lifecycle. By incorporating security practices early in the development process, organizations can reduce the risk of vulnerabilities and ensure that applications are secure from the start.
Impact of Emerging Trends on Data Protection
The emerging trends in secret server security have a significant impact on data protection. These trends can enhance security measures, improve threat detection, and automate security tasks.
- Enhanced Threat Detection: AI and ML can analyze vast amounts of data to identify patterns and anomalies that may indicate malicious activity. This can help organizations detect threats earlier and respond more effectively.
- Improved Security Posture: Zero trust security models help organizations improve their security posture by reducing their attack surface and requiring strong authentication for all users and devices.
- Increased Automation: AI and ML can automate security tasks, such as vulnerability scanning, incident response, and threat intelligence gathering. This can free up security teams to focus on more strategic tasks.
- Proactive Security: DevSecOps enables organizations to adopt a proactive security approach by integrating security into the development lifecycle. This can help prevent vulnerabilities from being introduced into applications in the first place.
Future of Secret Server Security
The future of secret server security is likely to be shaped by a combination of these emerging trends.
| Advancements | Challenges |
|---|---|
| Increased use of AI and ML for threat detection and response | Maintaining the security of AI and ML models themselves |
| Wider adoption of zero trust security models | Implementing and managing zero trust security effectively |
| Growth of cloud-native security solutions | Ensuring the security of data and applications in the cloud |
| Integration of DevSecOps practices | Building a strong DevSecOps culture within organizations |
Secret Server vs. Public Server
Secret servers and public servers are fundamentally different in their purpose, design, and security considerations. While public servers are designed for open access and widespread availability, secret servers prioritize confidentiality and restricted access. This distinction leads to significant differences in their security implementations.
Access Control
Access control mechanisms are paramount for both secret and public servers, but they differ significantly in their stringency and complexity.
- Secret servers employ highly restrictive access control measures, often involving multi-factor authentication, role-based access control (RBAC), and strict authorization policies. Only authorized personnel with specific clearance levels are granted access, and all actions are meticulously logged and monitored.
- Public servers, on the other hand, typically use less stringent access control mechanisms, allowing access to a wider range of users. While authentication is still required, it might be simpler and involve fewer security layers. This approach allows for greater accessibility but compromises security.
Data Protection
The level of data protection employed on secret servers far surpasses that of public servers.
- Secret servers typically utilize robust encryption techniques, both at rest and in transit, to safeguard sensitive data. This includes data encryption at the file level, database encryption, and network encryption protocols like TLS/SSL. Additionally, data backups are often stored in secure, off-site locations to ensure data integrity and availability even in the event of a security breach.
- Public servers often employ encryption, but it might not be as comprehensive or robust as on secret servers. Data might be encrypted at rest, but encryption in transit might not be mandatory, especially for less sensitive information. Additionally, data backups might be stored in the same location as the primary server, making them vulnerable to the same security threats.
Monitoring
Continuous monitoring is essential for both types of servers, but the scope and intensity of monitoring differ significantly.
- Secret servers undergo constant, real-time monitoring for suspicious activity, including intrusion attempts, unauthorized access, and data breaches. Intrusion detection systems (IDS), security information and event management (SIEM) systems, and security audits are crucial components of a robust monitoring strategy.
- Public servers typically rely on less intensive monitoring, often focusing on system performance and resource utilization. While security events are monitored, the level of scrutiny might be less stringent compared to secret servers.
Advantages and Disadvantages
Secret Servers
- Advantages:
- Enhanced security through robust access control, data encryption, and comprehensive monitoring.
- Protection of sensitive data, ensuring confidentiality and integrity.
- Reduced risk of data breaches and unauthorized access.
- Disadvantages:
- Increased complexity and cost associated with implementing and maintaining stringent security measures.
- Limited accessibility, which can hinder collaboration and information sharing.
Public Servers
- Advantages:
- Wide accessibility, allowing for easy sharing of information and resources.
- Lower implementation and maintenance costs compared to secret servers.
- Disadvantages:
- Increased risk of data breaches and unauthorized access due to less stringent security measures.
- Limited protection for sensitive data, potentially compromising confidentiality and integrity.
Last Recap
In the ever-evolving landscape of cybersecurity, secret servers stand as guardians of sensitive information. Understanding their intricacies, implementing robust security measures, and staying abreast of emerging threats is paramount. By embracing best practices and staying vigilant, organizations can ensure the safety and integrity of their critical data within the hidden world of secret servers.
A secret server can be a great place to store your digital creations, especially if you’re into crafting things. You can find inspiration and tutorials for all sorts of crafts at craft things , and then safely store your project files on your secret server.
This way, your creative projects are always accessible and protected.

