Ubuntu Proxy, a powerful networking tool, offers a range of benefits for users seeking enhanced security, privacy, and control over their internet traffic. Whether you’re a seasoned developer or a casual user, understanding how to leverage Ubuntu proxies can significantly improve your online experience.
This guide delves into the world of Ubuntu proxies, exploring their various types, configuration methods, and practical applications. We’ll cover everything from setting up a proxy server to configuring client applications and navigating common troubleshooting scenarios.
Introduction to Ubuntu Proxy
An Ubuntu proxy is a software application running on an Ubuntu operating system that acts as an intermediary between your computer and the internet. It intercepts all your internet traffic, allowing you to modify, control, or enhance your network connections.
A proxy server plays a crucial role in network security and privacy, providing benefits like enhanced security, anonymity, and content filtering. It acts as a shield between your device and the websites you visit, hiding your IP address and potentially blocking malicious websites.
Benefits of Using a Proxy on Ubuntu
Proxies offer several advantages for Ubuntu users, enhancing their online experience and improving security.
- Enhanced Security: Proxies can encrypt your internet traffic, making it difficult for third parties to intercept and monitor your online activities. This is particularly useful when using public Wi-Fi networks, where security is often compromised.
- Anonymity and Privacy: By routing your internet traffic through a proxy server, your actual IP address is masked, making it difficult to track your online activities. This is beneficial for maintaining your privacy and protecting your identity.
- Content Filtering: Proxies can be configured to block access to specific websites or content, providing control over what you and others on your network can access. This is particularly useful for restricting access to inappropriate or harmful websites.
- Bypass Geo-restrictions: Some websites restrict access based on geographical location. Proxies can help you bypass these restrictions by connecting you to servers in different locations, allowing you to access content that would otherwise be unavailable.
Common Use Cases for Ubuntu Proxies
Ubuntu proxies have various applications, depending on the user’s needs and objectives.
- Personal Use: Users can leverage proxies to enhance their online privacy, bypass geo-restrictions, and access blocked websites. They can also use them to improve security on public Wi-Fi networks.
- Business Use: Companies can use proxies to secure their network, control employee access to specific websites, and enforce security policies. They can also use them to bypass geo-restrictions for accessing international content.
- Development and Testing: Developers can use proxies to simulate different network conditions, test web applications, and debug network issues. They can also use them to access websites that are blocked or restricted in certain regions.
- Education: Schools and universities can use proxies to filter content, restrict access to inappropriate websites, and monitor student internet usage. They can also use them to provide secure access to online resources.
Types of Ubuntu Proxies
Proxies are intermediary servers that act as a bridge between your computer and the internet, forwarding your requests and receiving responses. They can be used for various purposes, including privacy, security, and bypassing restrictions. Ubuntu supports several types of proxies, each with its unique functionalities.
HTTP Proxies
HTTP proxies are the most common type of proxy. They operate at the application layer of the TCP/IP model, specifically for HTTP traffic. HTTP proxies are used to:
- Anonymize your browsing activity: By routing your traffic through the proxy server, your IP address is hidden from websites, making it difficult to track your online activities.
- Bypass restrictions: Some websites or networks might block access to certain websites or content. HTTP proxies can help circumvent these restrictions by acting as a gateway to the blocked resources.
- Cache web content: HTTP proxies can cache frequently accessed web content, speeding up subsequent requests for the same content.
HTTP proxies are commonly used for browsing the web, accessing restricted content, and enhancing privacy.
SOCKS Proxies
SOCKS proxies operate at the network layer of the TCP/IP model and can handle traffic from any application, not just HTTP. They are typically used for:
- Connecting to services that require a specific IP address: Some services, such as online gaming, might require a specific IP address to function correctly. SOCKS proxies can be used to connect to these services with a different IP address.
- Connecting to services that are blocked by firewalls: SOCKS proxies can bypass firewalls by forwarding traffic through a different network.
SOCKS proxies are often used for applications that require a specific IP address or need to bypass firewalls.
Transparent Proxies
Transparent proxies are a type of proxy that intercepts and forwards traffic without the user’s knowledge or intervention. They are often used by organizations to:
- Control internet access: Transparent proxies can be used to block access to specific websites or content.
- Monitor internet usage: Transparent proxies can log all internet traffic, allowing organizations to monitor employee activity.
- Filter content: Transparent proxies can be used to filter out inappropriate or harmful content.
Transparent proxies are commonly used by organizations to manage and monitor internet access for their employees.
Choosing the Right Proxy Type, Ubuntu proxy
The choice of proxy type depends on your specific needs. If you need to anonymize your browsing activity or bypass restrictions, an HTTP proxy is a good option. If you need to connect to services that require a specific IP address or bypass firewalls, a SOCKS proxy is a better choice. Transparent proxies are typically used by organizations for management and security purposes.
Setting Up a Proxy Server on Ubuntu
A proxy server acts as an intermediary between your clients and the internet, enabling you to control and enhance network traffic. Setting up a proxy server on Ubuntu is a straightforward process, allowing you to implement various security, performance, and access control measures.
Proxy Server Software Options
Several proxy server software options are available for Ubuntu, each offering unique features and functionalities. Here’s a breakdown of some popular choices:
- Squid: A widely used open-source proxy server known for its reliability, performance, and extensive features. It’s highly configurable and supports various protocols, including HTTP, HTTPS, FTP, and more. Squid is particularly suitable for caching web content, reducing bandwidth consumption, and enhancing website loading speeds.
- Nginx: A high-performance web server that can also function as a proxy server. Nginx is known for its efficiency, scalability, and support for various proxy features, including reverse proxying, load balancing, and content caching. It’s a popular choice for websites and applications requiring high traffic handling capabilities.
- Apache: Another widely used web server that can act as a proxy server. Apache is highly customizable and supports a wide range of features, including reverse proxying, content caching, and access control. It’s a versatile option for various proxy server needs, but it might not be as efficient as Nginx for high-traffic scenarios.
Installing and Configuring Squid
Squid is a popular choice for proxy servers due to its extensive features and robust performance. Here’s a step-by-step guide to installing and configuring Squid on Ubuntu:
- Install Squid: Use the following command to install Squid on your Ubuntu system:
sudo apt update && sudo apt install squid
- Configure Squid: The Squid configuration file is located at /etc/squid/squid.conf. Open this file using your preferred text editor and make the necessary modifications. Here are some essential configuration settings:
- http_port: Specify the port on which Squid will listen for HTTP traffic. The default port is 3128. For example:
http_port 3128
- cache_mem: Set the amount of memory allocated for caching web content. This value should be adjusted based on your server’s memory capacity and traffic volume. For example:
cache_mem 256 MB
- cache_dir: Define the directory where Squid will store cached web content. For example:
cache_dir ufs /var/spool/squid 1024 16 256
- access_log: Specify the path to the access log file, which records all HTTP requests handled by Squid. For example:
access_log /var/log/squid/access.log
- acl: Define access control lists (ACLs) to control which clients can access the proxy server. You can create ACLs based on IP addresses, hostnames, or other criteria. For example:
acl localnet src 192.168.0.0/16
http_access allow localnet
http_access deny allThis ACL allows access to the proxy server from clients within the 192.168.0.0/16 network and denies access to all other clients.
- http_port: Specify the port on which Squid will listen for HTTP traffic. The default port is 3128. For example:
- Restart Squid: After making the necessary configuration changes, restart Squid to apply them:
sudo systemctl restart squid
Installing and Configuring Nginx
Nginx is a highly efficient web server that can also act as a proxy server. Here’s how to install and configure Nginx on Ubuntu:
- Install Nginx: Use the following command to install Nginx on your Ubuntu system:
sudo apt update && sudo apt install nginx
- Configure Nginx: The Nginx configuration file is located at /etc/nginx/nginx.conf. Open this file using your preferred text editor and make the necessary modifications. Here are some essential configuration settings for using Nginx as a proxy server:
- upstream: Define an upstream server block to specify the backend servers that the proxy server will forward requests to. For example:
upstream backend
server 192.168.1.100:80;
server 192.168.1.101:80; - server: Create a server block to configure the proxy server’s virtual host. Within the server block, use the location directive to define the proxy settings for specific URLs or paths. For example:
server
listen 80;
server_name example.com;location /
proxy_pass http://backend;This configuration forwards requests to the backend upstream server block for all URLs under the example.com domain.
- upstream: Define an upstream server block to specify the backend servers that the proxy server will forward requests to. For example:
- Restart Nginx: After making the necessary configuration changes, restart Nginx to apply them:
sudo systemctl restart nginx
Installing and Configuring Apache
Apache is another versatile web server that can function as a proxy server. Here’s how to install and configure Apache on Ubuntu:
- Install Apache: Use the following command to install Apache on your Ubuntu system:
sudo apt update && sudo apt install apache2
- Configure Apache: The Apache configuration file is located at /etc/apache2/apache2.conf. Open this file using your preferred text editor and make the necessary modifications. Here are some essential configuration settings for using Apache as a proxy server:
- ProxyPass: Use the ProxyPass directive to specify the URL or path that the proxy server will forward requests to. For example:
ProxyPass /backend http://192.168.1.100:80/
This configuration forwards requests to the URL http://192.168.1.100:80/ for all URLs under the /backend path.
- ProxyPassReverse: Use the ProxyPassReverse directive to ensure that the proxy server correctly handles URL rewrites and redirects. For example:
ProxyPassReverse /backend http://192.168.1.100:80/
- ProxyPass: Use the ProxyPass directive to specify the URL or path that the proxy server will forward requests to. For example:
- Restart Apache: After making the necessary configuration changes, restart Apache to apply them:
sudo systemctl restart apache2
Configuring Ubuntu Clients to Use a Proxy
Once your Ubuntu proxy server is up and running, you need to configure your Ubuntu clients to use it. This ensures that all internet traffic from these clients is routed through the proxy, providing security, control, and potentially improved performance.
Configuring Proxy Settings in Web Browsers
Web browsers are the most common applications that require proxy settings. Here’s how to configure them:
- Firefox:
- Open Firefox and navigate to “Edit” > “Preferences”.
- Select the “Network” tab and click on “Settings” under “Connection”.
- Choose “Manual proxy configuration”.
- Enter the “HTTP Proxy” address (e.g., 192.168.1.100:8080) and the “Port” number.
- If your proxy requires authentication, check “Use this proxy server for all protocols” and enter the “Username” and “Password” in the provided fields.
- Click “OK” to save the changes.
- Chrome/Chromium:
- Open Chrome and navigate to “Settings”.
- Scroll down to the bottom and click on “Advanced”.
- Under “System”, click on “Open proxy settings”.
- In the “Internet Properties” window, navigate to the “Connections” tab and click on “LAN settings”.
- Check the “Use a proxy server for your LAN” box.
- Enter the “Address” (e.g., 192.168.1.100) and the “Port” number of your proxy server.
- If your proxy requires authentication, check “Bypass proxy server for local addresses” and enter the “Username” and “Password” in the provided fields.
- Click “OK” to save the changes.
Configuring Proxy Settings in Other Applications
Many other applications, such as email clients, FTP clients, and download managers, might also require proxy settings. These settings are often found in the application’s “Preferences” or “Settings” menus. Look for options related to “Proxy”, “Network”, or “Connection”.
Automatic Proxy Detection and Configuration
Ubuntu supports automatic proxy detection and configuration using the “pac” (Proxy Auto-Config) protocol. This allows you to automatically detect and use the appropriate proxy based on your network settings.
- PAC File:
- You can configure your Ubuntu system to use a PAC file by setting the “http_proxy” environment variable to the URL of the PAC file. For example:
export http_proxy=http://your-proxy-server/pac.js
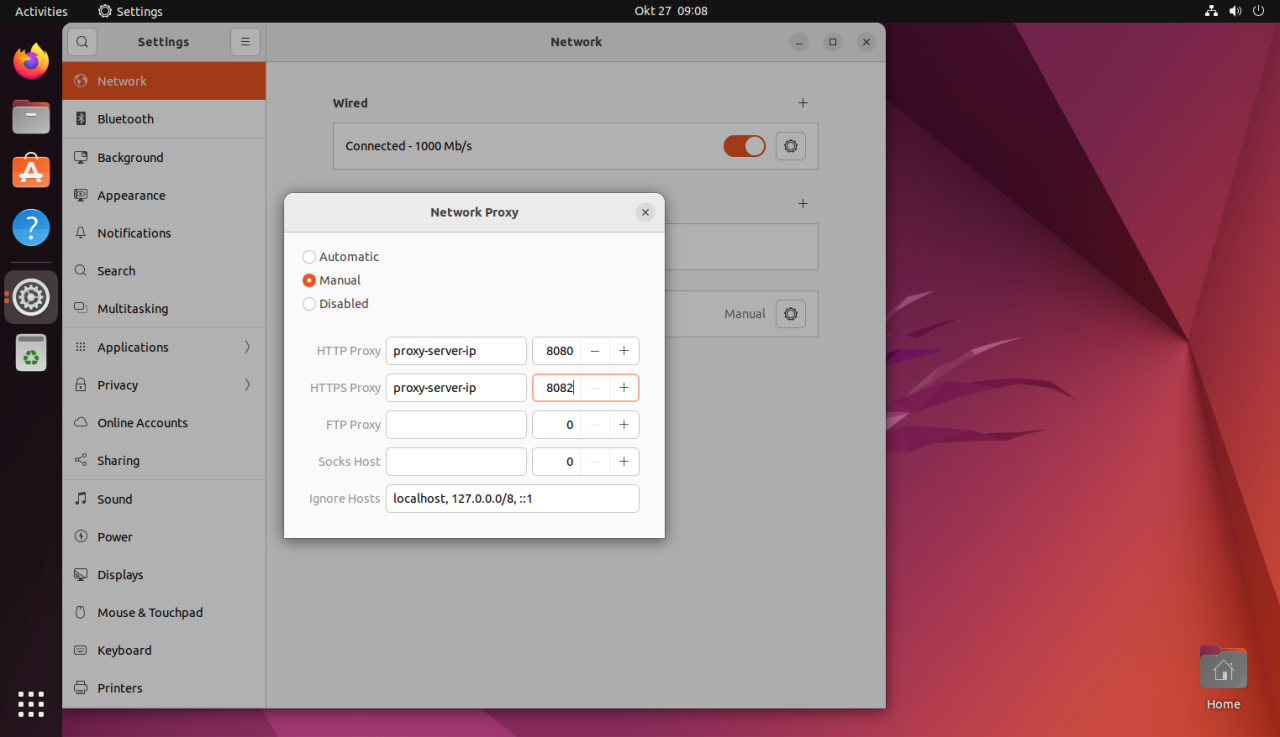
- You can also configure the PAC file using the “Network Proxy” settings in the “System Settings” application. Go to “Network” > “Network Proxy” and select “Automatic proxy configuration”. Enter the URL of your PAC file and click “Apply”.
- You can configure your Ubuntu system to use a PAC file by setting the “http_proxy” environment variable to the URL of the PAC file. For example:
- WPAD (Web Proxy Auto-Discovery):
- Ubuntu also supports automatic proxy detection using the “WPAD” protocol. This protocol allows your system to automatically discover the proxy server address from your network.
- To enable WPAD, you can configure the “http_proxy” environment variable to “auto”. For example:
export http_proxy=auto
Proxy Security and Privacy
Proxies, while useful for various purposes, introduce additional security and privacy considerations. It’s crucial to understand these aspects and implement appropriate measures to protect your data and maintain privacy when using proxies on Ubuntu.
Securing a Proxy Server
Securing a proxy server is paramount to protect sensitive information and prevent unauthorized access. Here are essential steps:
- Enable HTTPS: Configure your proxy server to use HTTPS, ensuring secure communication between clients and the server. This encrypts data transmission, making it difficult for eavesdroppers to intercept sensitive information.
- Use Strong Passwords: Implement strong passwords for administrative access to the proxy server, making it harder for unauthorized individuals to gain control.
- Limit Access: Restrict access to the proxy server to authorized users or devices. This can be done through IP address whitelisting or using access control lists (ACLs).
- Regular Updates: Keep the proxy server software and its dependencies updated to patch vulnerabilities and enhance security.
- Firewall Configuration: Configure a firewall to block unauthorized access to the proxy server, protecting it from malicious attacks.
- Security Audits: Regularly perform security audits to identify potential vulnerabilities and implement necessary mitigation strategies.
Securing Client Connections
Securing client connections to a proxy server is equally important to safeguard user data and privacy. Here’s how:
- Use a Secure Proxy: Prefer using a proxy server that offers secure communication protocols like HTTPS. This ensures data is encrypted during transmission.
- Configure Proxy Settings: Configure your Ubuntu client to use the proxy server correctly. Incorrect configurations can leave your connection vulnerable.
- Use a VPN: Consider using a Virtual Private Network (VPN) in conjunction with a proxy server. A VPN encrypts all your internet traffic, providing an additional layer of security and privacy.
- Beware of Public Proxies: Public proxies can be insecure and may expose your data to risks. Use them with caution and only for trusted websites.
Maintaining Privacy While Using a Proxy
While proxies can enhance privacy, it’s crucial to implement best practices to maintain privacy:
- Choose a Reputable Proxy Provider: Select a proxy provider with a strong privacy policy and a reputation for data security. Avoid using proxies that log user activity or sell data to third parties.
- Minimize Data Sharing: Limit the amount of personal information you share when using a proxy. Avoid using social media accounts or accessing sensitive websites through a public proxy.
- Use a Separate Browser: Consider using a separate web browser dedicated to accessing the internet through a proxy. This helps isolate your browsing activity and reduces the risk of tracking.
- Clear Browsing History and Cookies: Regularly clear your browsing history and cookies to prevent websites from tracking your online activities.
Common Ubuntu Proxy Use Cases
Ubuntu proxies are versatile tools with a wide range of applications, offering benefits for both individuals and organizations. They can be used to enhance network security, control access to specific content, and optimize network traffic.
Network Access Control
Proxies play a crucial role in controlling access to the network. They act as intermediaries, filtering traffic and preventing unauthorized access.
- Restricting access to specific websites or services: Proxies can be configured to block access to certain websites or services, enhancing network security by preventing employees from accessing inappropriate content or malicious websites. For instance, an organization might block access to social media platforms during working hours to improve productivity.
- Implementing user authentication: Proxies can require users to authenticate before granting them access to the network. This ensures that only authorized individuals can access network resources. For example, a company might require employees to log in with their credentials before accessing internal applications or files.
- Limiting bandwidth usage: Proxies can help control bandwidth usage by setting limits on the amount of data that users can download or upload. This is particularly useful in environments with limited bandwidth, such as schools or small businesses.
Content Filtering
Proxies can filter content based on various criteria, including s, categories, and websites. This allows organizations to control the content that employees or students can access.
- Blocking inappropriate content: Proxies can block access to websites containing offensive or inappropriate content, such as pornography, hate speech, or violence. This is particularly important in schools and workplaces where it is essential to protect minors or maintain a professional environment.
- Filtering content based on s: Proxies can filter content based on specific s, allowing organizations to block access to websites containing sensitive information or topics. For example, a company might block access to websites containing competitor information or financial data.
- Restricting access to specific categories: Proxies can block access to specific categories of websites, such as social media, gaming, or shopping. This can help improve productivity and reduce distractions in the workplace.
Traffic Optimization
Proxies can optimize network traffic by caching frequently accessed content and compressing data. This can improve performance and reduce bandwidth usage.
- Caching frequently accessed content: Proxies can cache frequently accessed content, such as web pages, images, and videos. This reduces the need to download the same content multiple times, improving performance and reducing bandwidth usage.
- Compressing data: Proxies can compress data before sending it to clients, reducing the amount of data that needs to be transmitted. This can improve performance and reduce bandwidth usage, especially for large files or websites with many images or videos.
- Load balancing: Proxies can distribute traffic across multiple servers, ensuring that no single server becomes overloaded. This improves performance and reliability by preventing bottlenecks and ensuring that all users have a smooth experience.
Troubleshooting Ubuntu Proxy Issues
Setting up and using a proxy server on Ubuntu can sometimes present challenges. This section explores common problems encountered when configuring and utilizing Ubuntu proxies, along with effective troubleshooting techniques to address proxy errors and connectivity issues.
Common Proxy Problems
Proxy problems can stem from various sources, ranging from incorrect configurations to network connectivity issues. Here are some frequently encountered problems:
- Incorrect Proxy Settings: Misconfigured proxy settings on the client or server can prevent successful connections. This could involve incorrect IP addresses, ports, usernames, or passwords.
- Firewall Restrictions: Firewalls on the client, server, or network can block proxy traffic, preventing access to external resources.
- Network Connectivity Issues: Problems with the network infrastructure, such as a faulty router or internet service disruptions, can lead to proxy connectivity problems.
- Proxy Server Errors: The proxy server itself might experience errors or outages, making it unavailable to clients.
- Proxy Authentication Issues: If the proxy requires authentication, incorrect credentials or authentication failures can disrupt access.
Troubleshooting Techniques
When troubleshooting proxy issues, a systematic approach can help isolate and resolve the problem efficiently.
- Verify Proxy Settings: Double-check the proxy settings on both the client and server to ensure they are accurate and consistent. This includes the IP address, port number, username, and password (if applicable).
- Check Network Connectivity: Test network connectivity by pinging the proxy server and other external websites. If there are network issues, try restarting the network interface or router.
- Disable Firewalls Temporarily: To determine if firewalls are blocking proxy traffic, temporarily disable them on the client and server. If the problem resolves, configure the firewall rules to allow proxy traffic.
- Test Proxy Server Availability: Verify that the proxy server is operational by accessing it directly from a browser or using a proxy testing tool.
- Check Proxy Logs: Examine the proxy server logs for any error messages or unusual activity that might indicate the source of the problem.
- Use Proxy Diagnostics Tools: Utilize specialized proxy diagnostic tools to identify and troubleshoot common proxy issues. These tools can help pinpoint problems related to connectivity, authentication, or server configuration.
Resources for Proxy Troubleshooting
For more in-depth troubleshooting guidance and solutions, consult the following resources:
- Ubuntu Documentation: The official Ubuntu documentation provides detailed information on setting up and configuring proxy servers and clients.
- Online Forums: Numerous online forums and communities dedicated to Ubuntu and networking offer a platform for asking questions and seeking assistance from experienced users.
- Proxy Server Documentation: Refer to the documentation for the specific proxy server software you are using for troubleshooting tips and error codes.
- Network Monitoring Tools: Tools like Wireshark can help analyze network traffic to identify potential problems related to proxy communication.
Advanced Ubuntu Proxy Configuration
Beyond the basic setup, Ubuntu’s proxy capabilities offer a range of advanced features for fine-tuning performance and security. This section explores some of these options, providing insights into customizing proxy behavior and enhancing its functionality.
Proxy Caching
Proxy caching is a fundamental technique for optimizing network performance. It involves storing frequently accessed web content on the proxy server, allowing subsequent requests for the same content to be served directly from the cache, reducing latency and bandwidth consumption.
- Squid Proxy: Squid is a popular open-source caching proxy server commonly used with Ubuntu. It offers various caching mechanisms, including disk caching, memory caching, and hierarchical caching, allowing you to configure caching behavior based on your specific needs.
- Caching Policies: Squid provides flexible caching policies that control which content is cached, how long it’s cached, and how it’s retrieved. You can define policies based on content type, file size, request frequency, and other factors.
- Cache Management: Squid offers tools for monitoring and managing the cache, allowing you to view cache statistics, purge outdated content, and optimize cache performance.
Proxy Authentication
Authentication mechanisms secure proxy access, ensuring only authorized users can utilize the proxy server. This is particularly crucial in corporate or sensitive environments where access control is paramount.
- Basic Authentication: This simple method uses a username and password combination for authentication. However, it transmits credentials in plain text, making it less secure for sensitive data.
- Digest Authentication: Digest authentication is more secure than basic authentication as it uses a one-way hash function to protect credentials during transmission.
- NTLM Authentication: NTLM authentication is commonly used in Windows environments and provides a more robust authentication method for proxy access.
Proxy Logging and Monitoring
Comprehensive logging and monitoring are essential for understanding proxy activity, troubleshooting issues, and ensuring security.
- Squid Logging: Squid provides detailed logging capabilities, allowing you to track various proxy events, including successful requests, failed requests, authentication attempts, and cache hits. You can configure log levels, specify log formats, and define log rotation policies.
- Proxy Monitoring Tools: Tools like SquidGuard and SquidAnalyzer can be used to analyze proxy logs, generate reports, and gain insights into proxy usage patterns, security threats, and performance bottlenecks.
Proxy Performance Tuning
Optimizing proxy performance is crucial for ensuring efficient network operations. This involves fine-tuning various settings and configurations.
- Connection Limits: Configure the maximum number of concurrent connections the proxy server can handle to prevent resource exhaustion and improve responsiveness.
- Cache Size: Adjust the cache size based on your network’s traffic volume and content access patterns. Larger caches can store more content but consume more disk space.
- Network Bandwidth Allocation: Prioritize bandwidth allocation to critical applications or services, ensuring optimal performance for essential tasks.
Proxy Security Measures
Securing the proxy server is essential to prevent unauthorized access, malicious activities, and data breaches.
- Firewall Rules: Configure firewall rules to restrict access to the proxy server, allowing only authorized connections. Implement a strong firewall policy to prevent unauthorized access and malicious traffic.
- Access Control Lists (ACLs): ACLs can be used to define specific access rules based on user identity, IP address, or other criteria. This allows you to control which users or devices can access specific resources or websites through the proxy.
- Content Filtering: Employ content filtering techniques to block access to malicious websites, unwanted content, or specific domains. SquidGuard can be used to implement content filtering rules based on various criteria.
Ubuntu Proxy Alternatives
While setting up a traditional proxy server on Ubuntu is a powerful option, it’s not the only way to achieve the benefits of proxy usage. Several alternative solutions offer varying levels of functionality and ease of use, catering to diverse needs and preferences.
Cloud-Based Proxy Services
Cloud-based proxy services offer a convenient and often cost-effective way to leverage the benefits of a proxy without the complexities of server setup and maintenance. These services are typically hosted on remote servers, accessible through a user-friendly interface.
- Ease of Use: These services abstract away the technical complexities of setting up and managing a proxy server, making them accessible to users with varying levels of technical expertise.
- Scalability: Cloud-based services can easily scale to accommodate fluctuating traffic demands, ensuring consistent performance.
- Cost-Effectiveness: Many cloud-based proxy services offer pay-as-you-go pricing models, making them a cost-effective option, especially for occasional or low-volume usage.
- Examples: Some popular cloud-based proxy services include:
- Proxify: A service that offers a wide range of proxy options, including residential, data center, and mobile proxies, catering to various use cases.
- Smartproxy: A service known for its high-quality residential proxies, suitable for tasks like web scraping and social media automation.
- Luminati: A provider specializing in high-performance proxies, ideal for demanding tasks like large-scale data collection.
Proxy Extensions for Browsers
Browser extensions offer a simple and readily available way to enhance your browsing experience with proxy functionality. These extensions typically integrate seamlessly with your browser, allowing you to easily switch between different proxy servers or configure specific proxy settings.
- Convenience: Proxy extensions are readily available from browser stores and offer a user-friendly interface for managing proxy settings.
- Privacy and Security: Some extensions offer built-in features for enhancing privacy and security, such as encrypting your traffic or blocking unwanted trackers.
- Examples: Popular browser proxy extensions include:
- Hola VPN: A free extension that allows you to browse the internet from different locations, effectively changing your IP address.
- Zenmate: A paid extension that offers a range of proxy features, including encryption and website blocking, for enhanced privacy and security.
- CyberGhost: A popular VPN service that also offers a browser extension for accessing its proxy network and other features.
VPN Services
Virtual Private Networks (VPNs) provide a secure and encrypted connection between your device and a remote server, effectively masking your IP address and location. While not strictly a proxy, VPNs offer similar benefits, including enhanced privacy, security, and access to geo-restricted content.
- Enhanced Privacy: VPNs encrypt your internet traffic, making it difficult for third parties to monitor your online activity.
- Security: VPNs can protect your connection from unauthorized access, especially when using public Wi-Fi networks.
- Access to Geo-Restricted Content: VPNs can allow you to access content that is blocked in your location by connecting you to a server in a different country.
- Examples: Some popular VPN services include:
- NordVPN: A well-established VPN provider with a wide network of servers and strong security features.
- ExpressVPN: A popular VPN service known for its fast speeds and user-friendly interface.
- Surfshark: A VPN provider that offers unlimited simultaneous connections, making it suitable for multiple devices.
Final Thoughts
From basic principles to advanced configurations, this comprehensive guide equips you with the knowledge and skills to effectively utilize Ubuntu proxies for a secure and efficient internet journey. By understanding the nuances of proxy technology, you can unlock a world of possibilities and optimize your online experience.
Setting up a proxy server on Ubuntu can be a great way to enhance security and control network access. If you’re working with SQL Server databases, you might find it helpful to use a tool like Microsoft Management Studio for managing your databases.
Once your proxy is configured, you can seamlessly connect to your SQL Server instance from your Ubuntu system using tools like Microsoft Management Studio.